Ready?
Before we start, a few points of order.
Points of order

For people watching the livestream or anyone in the audience who would prefer subtitles, the transcript, slides, and supporting materials for this talk are now live at nfc.toys.
We're covering a lot in this talk, and it clocks in at just under fifty minutes, which means we don't have time for live Q&A. But, Q&A is important, so I will be taking questions on paper and electronically. The in-person audience can write their questions on the flip side of their feedback form. Both the in-person and livestream audiences can submit questions via Twitter to @nfctoys, or via text message for the remainder of the day only to +1-856-2-NFC-QNA. There are slide numbers on each slide you can reference. I will post answers to questions on nfc.toys, and reply to you with a link to your answer. If you're watching this talk in the future, asking questions via Twitter will be your best bet for a response.

This is an introductory level talk, but there were also more advanced and related talks at HOPE this year:
- Being able to do things you want with things you own, even if they have electronics or software inside them, is a core tenet of the Right to Repair, and there was a Right to Repair panel on Friday. Watch the recording of the panel (fast-forward to 48:30).
- The Electronic Frontier Foundation is suing the federal government over DMCA section 1201 and they also had a panel, Ask the EFF: The Year in Digital Civil Liberties on Saturday. Watch the recording of the panel.
- James Chambers presented more in-depth, technical work on Nintendo Amiibo toys in Breath of the RF Field: Hacking Amiibo with Software-Defined Radio on Saturday. Watch the recording of the talk (fast-forward to 12:07:00).
In addition, at HOPE X in 2014, artist Joshua Fried put forth the idea that skeuomorphism, often experienced as extreme, historical realism, may offer a natural home for steganography, the practice of hiding messages in plain sight. Likewise, NFC toys offer the ability to store digital content, undetected inside a figurine, stuffed animal, playing card, or box of cereal. Hear more in his talk, Skeuomorphic Steganography.
Finally, for the in-person audience, I've provided speaker feedback forms and pens. One side is for Q&A, the other is for talk or speaker feedback. Please fill these out at the end and pass them forward, it helps me understand how this went, independent of any feedback you may provide HOPE directly. If you need paper for your own notes, I've also provided blank index cards, so please use the feedback forms to ask questions and provide feedback.
What NFC is
We're going to talk about NFC toys, which are toys, which have NFC tags embedded in them. I want to give you an idea of why this is worth an hour of your time, but I need to start with a couple of examples for everyone who doesn't know what NFC is.

So, a show of hands, who has paid for something using an iPhone with Apple Pay,

or an Android phone with Google Pay?
Cool, hands down. NFC is how your phone talks to the payment terminal you hold it up to, and all those wireless payments systems work the same way under the hood. Part of NFC is a standard method of wireless communication.

Show of hands, who waves a security badge against a reader to get into their building at work? Cool, hands down. NFC is a subset of the RFID technology that your badge probably uses.
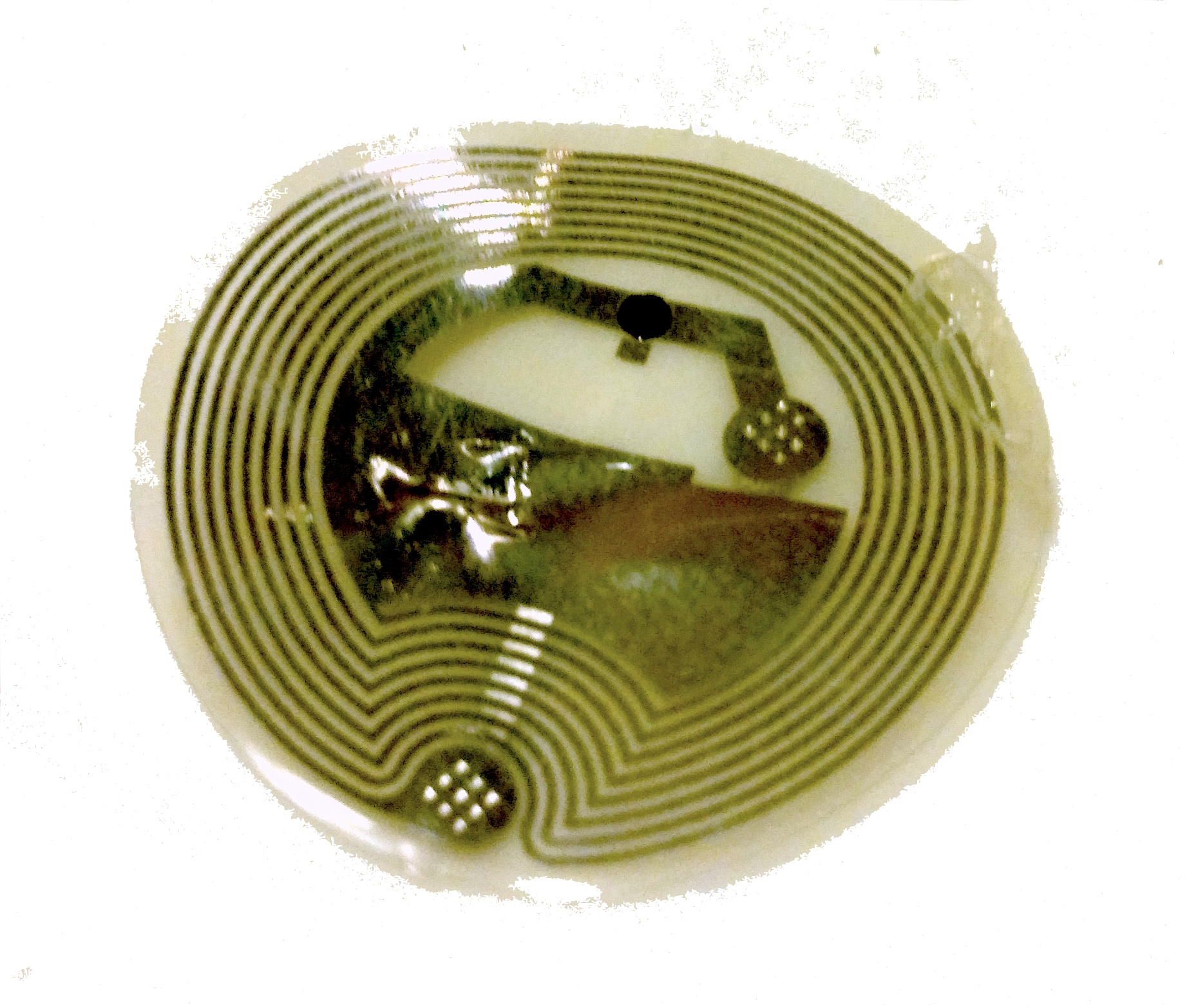
Inside that badge, just like inside an NFC toy, is what's called a tag. NFC tags are a small amount of memory, logic, and an antenna. They're not really a full-on microprocessor. NFC tags are more like tiny, slow, wireless flash drives. Part of NFC is a standard set of tag types.
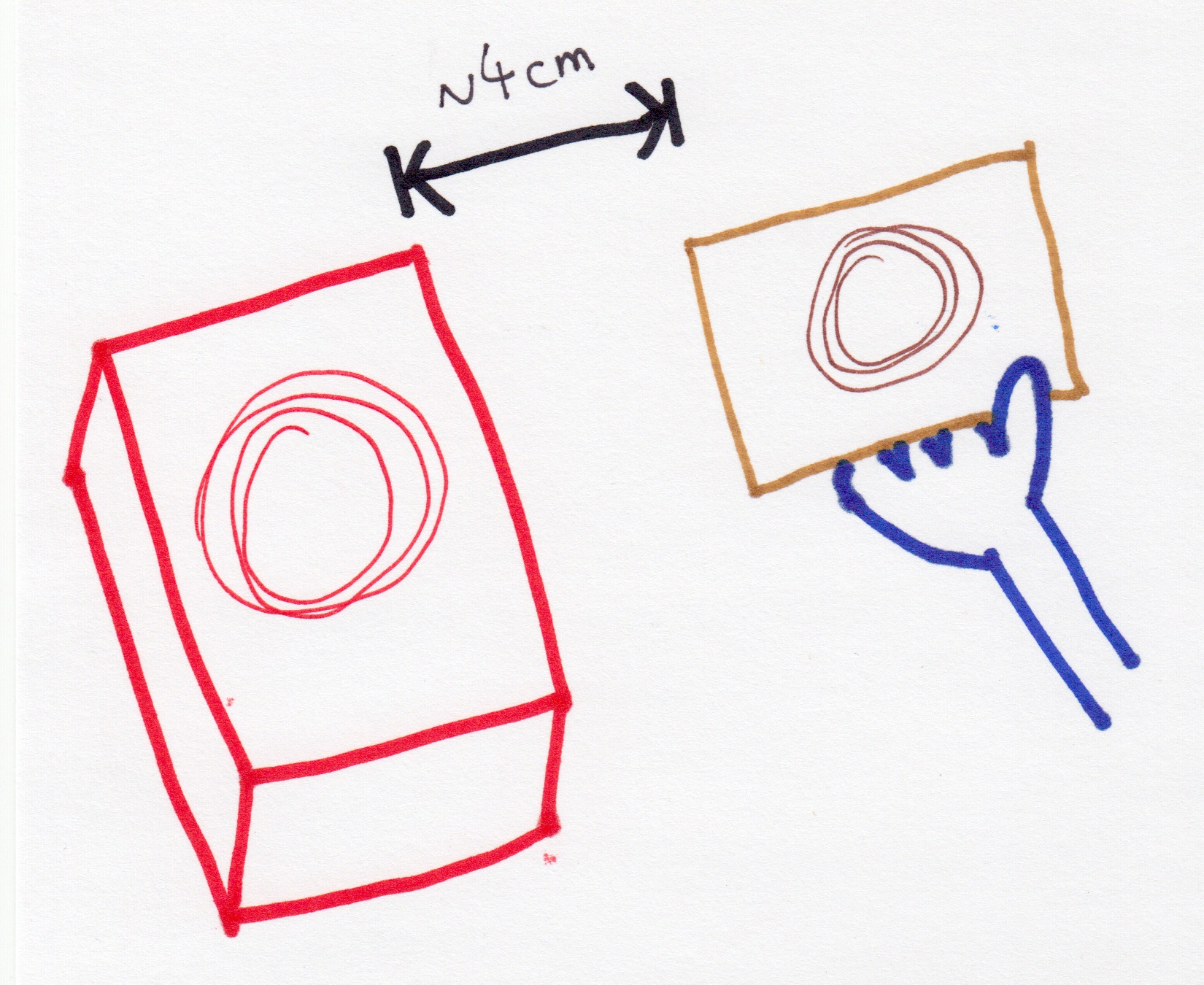
When a tag, or your phone talking like a tag, is near enough to a reader, generally millimeters to centimeters,
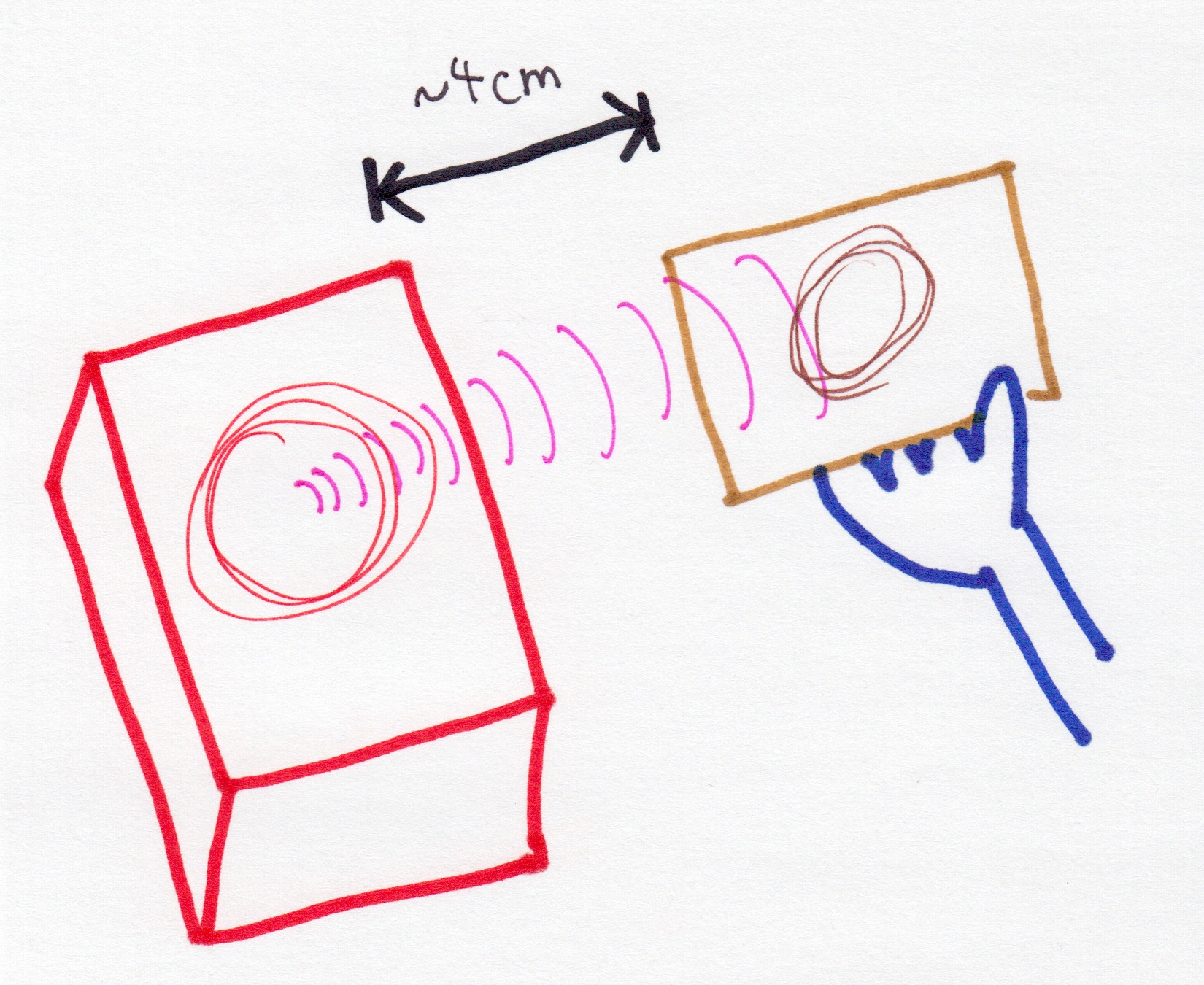
the reader's radio frequency transmissions provide enough wireless power
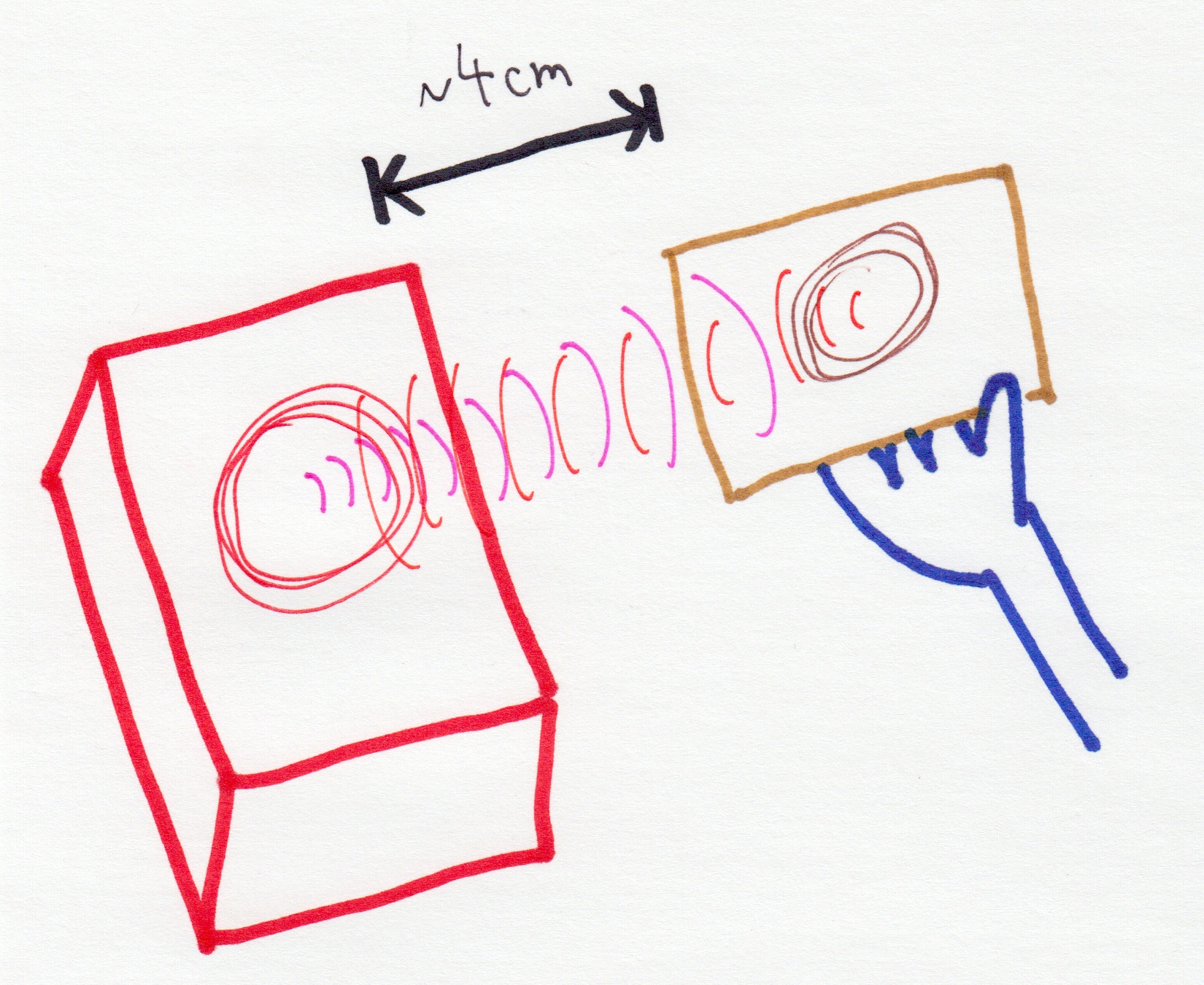
to allow the tag to communicate back and forth, often just tens to a few hundred bytes.
Why NFC toys


Now, NFC tags which store tiny amounts of data, wireless NFC communication methods to transmit them, these are technical tools for engineers.

NFC toys are first and foremost toys.

Toys are meant to be fun.

Toys are meant to be played with.
Everyone understands that toys are toys, so when a toy does something that a toy wouldn't normally do, that's visually interesting, that's stimulating.
Swiping a toy of Samus Aran from Metroid on a subway turnstile? That perks you up, that's super interesting. What other kinds of data could you put on one?
Well, anything, because remember, they're like tiny, slow, wireless flash drives.

“Because you did not invite me, I tell you that in her fifteenth year, your daughter will prick herself with a spindle and fall over dead.”
You could have a Maleficent toy holding within it the original curse from the Grimm fairy tale.

https://archive.org/stream/peterwendy00barr2
You could have a Tinkerbell toy with a link to the ebook of Peter and Wendy.
(Disney Infinity was discontinued before a Peter Pan figure was released, but unreleased toys have made their way to online sellers.)

Address:
1NfCToYSmwwz7egVp9NSs3XSMLZiTzgZuNPrivkey:
5JWTJ699JaPRh2EjnVaNvAgcWvD2EqsvT9hExs3TA2G2sJBtVuF
You could have a piggy bank toy with your Bitcoin wallet's private key.

https://open.spotify.com/user/official_star_wars/playlist/0mJWJsZTz0I1iXFFeyRzcS
You could have a Kylo Ren toy with a playlist of emo songs.

You could have a toy car to unlock your real car.

Third place: England
Second place: France
First place: Croatia
You could have a Kickoff Countdown toy store your World Cup predictions.

40.7497723, -73.9906244
You could have a toy in a geocache, with coordinates to another geocache.

You could have a Pikachu toy with the credentials to your dev environment at work.

You could have a larger Pikachu toy with the credentials to your QA environment at work.

You could have a giant Pikachu toy with the credentials to your production environment at work.
Even though they're technically no different than a bare NFC tag, storing the same amount of data in the same way, communicating the same way, the novelty and playful aspect of NFC toys supports us in thinking about unique and fun uses for NFC tags in a way that NFC tags by themselves don't.

That said, while they're technically no different than a bare NFC tag, because NFC toys are often intended to support interactions with copyrighted, digital content, they may be legally different if we want to use them for our own purposes. We should be able to play with our toys as we see fit, and it's up to us to assert our rights to do so.
Talk outline

We're going to talk about three makes of NFC toys, with most of our time spent on Activision Skylanders, because that's where most of the literature is,

but we'll also cover Disney Infinity

and Nintendo Amiibo.

There are others makes of NFC toys, and the techniques we'll use can apply to them, but these are what we're talking about today.

As we talk about them, we're going to explain how they work, along with some background information about the toys-to-life genre of video games, and pertinent details about NFC tags in general.

We'll explore each one with off-the-shelf hardware and software, referencing a long history of security research, and learn how that exploration can lead to determining read/write credentials.

Then, we'll see how to write our own data to those three different types of NFC toy, and talk about the legal implications of doing so.
While I will be discussing legal matters, I am not a lawyer, and this is not legal advice.
Finally, I'll hand out NFC toys and worksheets for anyone in the audience who wants to try this out for themselves. I hope you will.
Activision Skylanders

We're going to start with Activision Skylanders.

A show of hands, who has kids who were into Skylanders, and you had to buy them a bunch of stupid toys and video games over the past seven years? Okay, hands down.
A show of hands, who was personally into Skylanders, and bought yourselves a bunch of awesome toys and video games over the past seven years? Fantastic, great.

For everyone else who isn't familiar with Skylanders, it's a video game that launched in 2011 as a Spyro the Dragon reboot, across every major platform, plus a Flash-based web game. It's a game in the toys-to-life genre, as in, bring your toys to life.

Each Skylanders game shipped with a few starter figures,

and a USB NFC reader styled as a "portal."

To play the game, you place a figure on the portal, and that's the character you play as.
When you name your character, and earn points and collect items, they're stored in the NFC tag in the toy,
so when you take that same toy to your friend's house, it shows up with the name you gave it, all its points and experience, and all its history.

While you can beat the game with what comes in the starter kit, to reach 100% completion, and to collect every achievement, you need to buy additional types of characters and expansion toys.
Skylanders was a huge success. Sequels were shipped every year, variously offering



with twice the NFC tags,

or vehicle figures, resulting in over 350 Skylanders NFC toys of all types.
Android phones

Earlier, we said that some Android phones, ones that support Google Pay, can talk NFC, and so an Android phone will be the first of three standard tools I'll be discussing.
When you're exploring NFC tags on your own, it's easiest to look for an Android phone with Google Pay support. (iPhones are restricted in terms of what types of tag and types of data they can read, and they can't write to them.) Any Android phone with NFC support can read any NFC Type 1 through 4 tag. However, the proprietary NXP MIFARE tags can only be read by phones with NFC chips manufactured by NXP. You should be able to find an older Android phone with NFC support for under $100. (There's also a recent NFC Type 5 tag, which I know nothing about, sorry.)
Skylanders and Android phones

So, what happens when we swipe an NFC toy against an appropriate Android phone?
This is a "Ninjini" figure from Activision Skylanders, when swiped against an Android phone with NFC support, running the app NFC Tools.
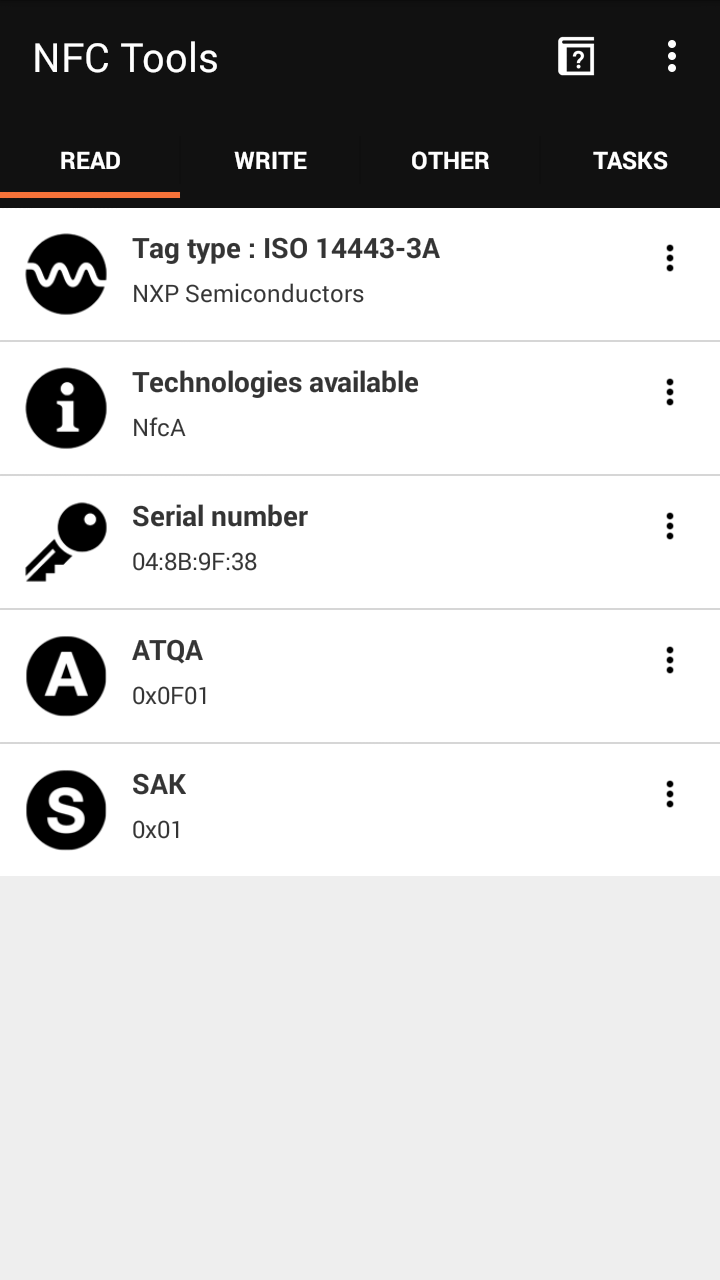
It gives us five pieces of information, as it should. Some of the expected uses for NFC are for things like business cards and advertisements, so some information can always be read from an NFC tag using standard tools, and these represent some of that standard, public information.
The first thing we see is it's an NXP brand tag. NXP is a major manufacturer of NFC tags, and they've promoted the use of their NFC tags in games like Skylanders since at least 2011.
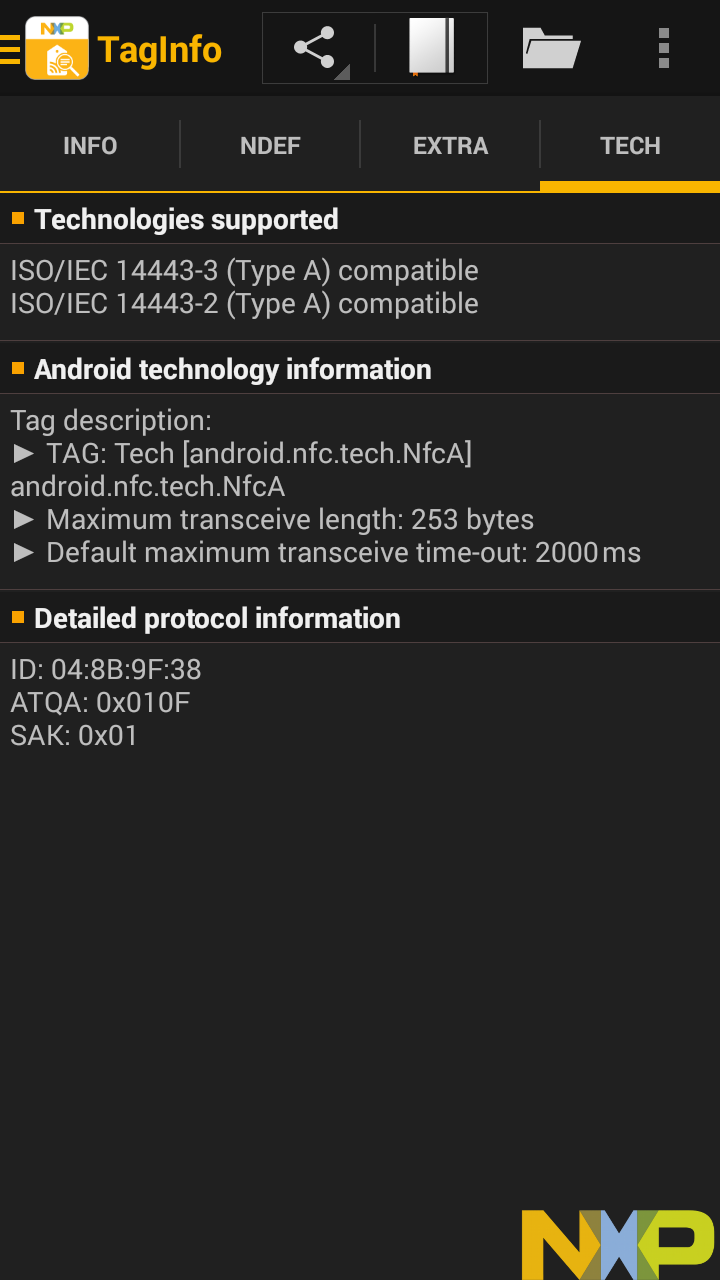
We also see the serial number for the tag, also called the UID, and the ATQA and SAK, which help identify the type of tag it is.

Since it's an NXP tag, let's see if NXP's own app, NXP TagInfo, can tell us anything more.
So, I gotta say, these screens are kinda empty.
They're not telling us much more than NFC Tools did, and that's actually a little unusual.
Other NFC tags and Android phones

Let me show you what some other NFC tags look like in the same NXP TagInfo app.
Here's a payment card for my local arcade.

While the first two screens are pretty bare,
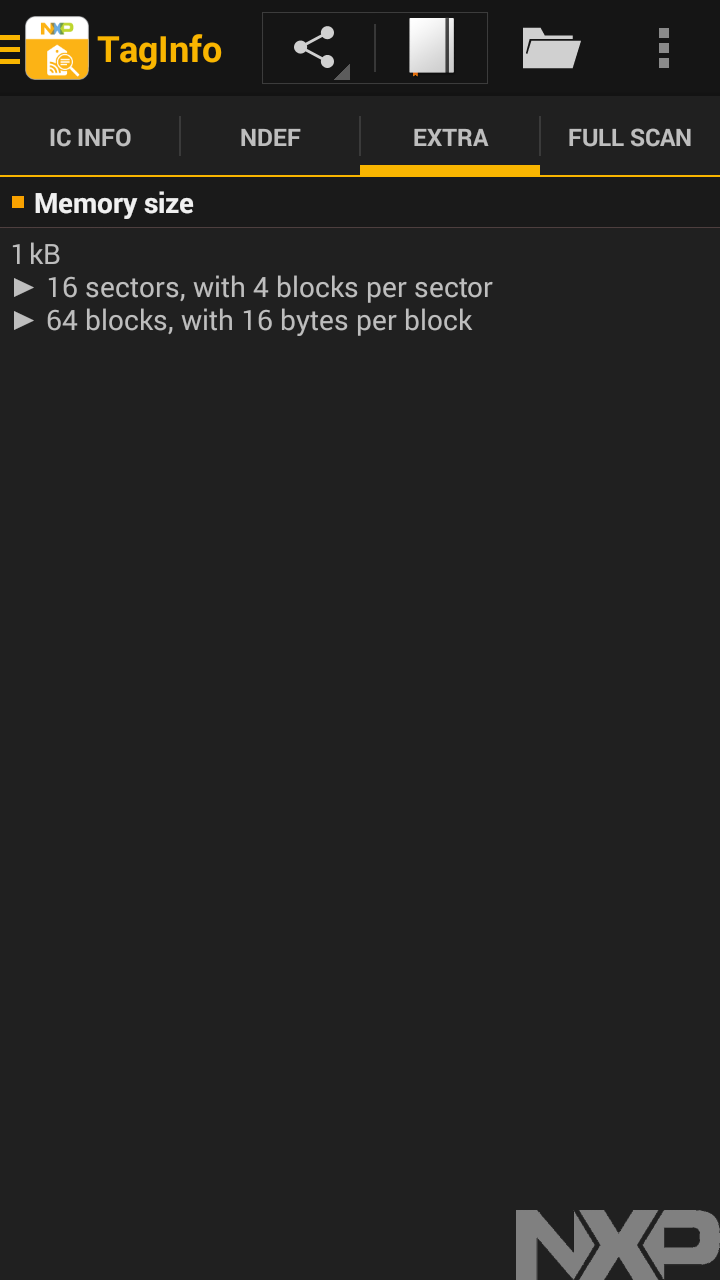
the third one shows us the memory size, which is how much storage the tag has, and how it's set up. The fourth one shows us the actual data on the card, and it formats it to match up with the description in the memory size.
Sector 0 (0x00)
[00] r-- 04 B1 13 F9 5F 08 04 00 01 EF 8F 5B 1C EE 27 1D |...._......[..'.|
[01] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[02] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[03] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 1 (0x01)
[04] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[05] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[06] rwi F3 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[07] wxx XX:XX:XX:XX:XX:XX FF:07:80 69 FF:FF:FF:FF:FF:FF
(unknown key) Factory default key (readable)
Sector 2 (0x02)
[08] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[09] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[0A] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[0B] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 3 (0x03)
[0C] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[0D] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[0E] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[0F] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 4 (0x04)
[10] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[11] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[12] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[13] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 5 (0x05)
[14] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[15] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[16] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[17] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 6 (0x06)
[18] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[19] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[1A] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[1B] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 7 (0x07)
[1C] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[1D] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[1E] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[1F] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 8 (0x08)
[20] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[21] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[22] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[23] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 9 (0x09)
[24] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[25] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[26] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[27] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 10 (0x0A)
[28] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[29] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[2A] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[2B] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 11 (0x0B)
[2C] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[2D] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[2E] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[2F] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 12 (0x0C)
[30] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[31] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[32] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[33] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 13 (0x0D)
[34] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[35] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[36] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[37] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 14 (0x0E)
[38] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[39] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[3A] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[3B] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
Sector 15 (0x0F)
[3C] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[3D] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[3E] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[3F] wxx FF:FF:FF:FF:FF:FF FF:07:80 69 FF:FF:FF:FF:FF:FF
Factory default key Factory default key (readable)
r/R=read, w/W=write, i/I=increment,
d=decr/transfer/restore, x=r+w, X=R+W
data block: r/w/i/d:key A|B, R/W/I:key B only,
I/i implies d, *=value block
trailer (order: key A, AC, key B): r/w:key A,
W:key B, R:key A|B, (r)=readable key
AC: W implies R+r, R implies r
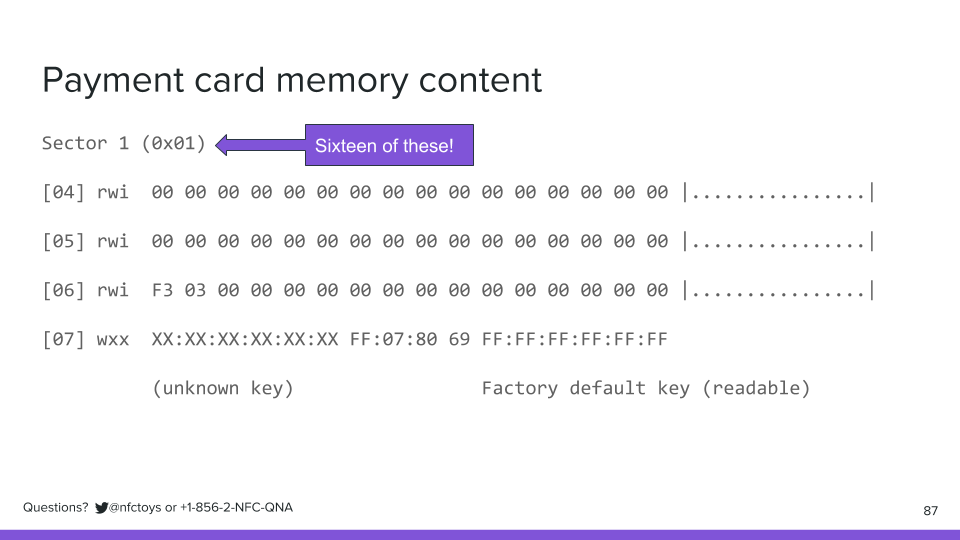
This is laid out just like the data is stored on the tag, in this case, sixteen sectors, with four rows of sixteen bytes each.
We can see that because along with the standard, public information that every tag presents, for NFC tags which can be protected, there are also standard keys and passwords that are commonly used, often to allow for public readers, while still restricting who can write to or update a tag. This tag uses a common, standard, factory default key, meaning anyone can see what's on it.

Here's a pair of Bluetooth headphones, which embed an NFC tag for easy pairing with your phone.
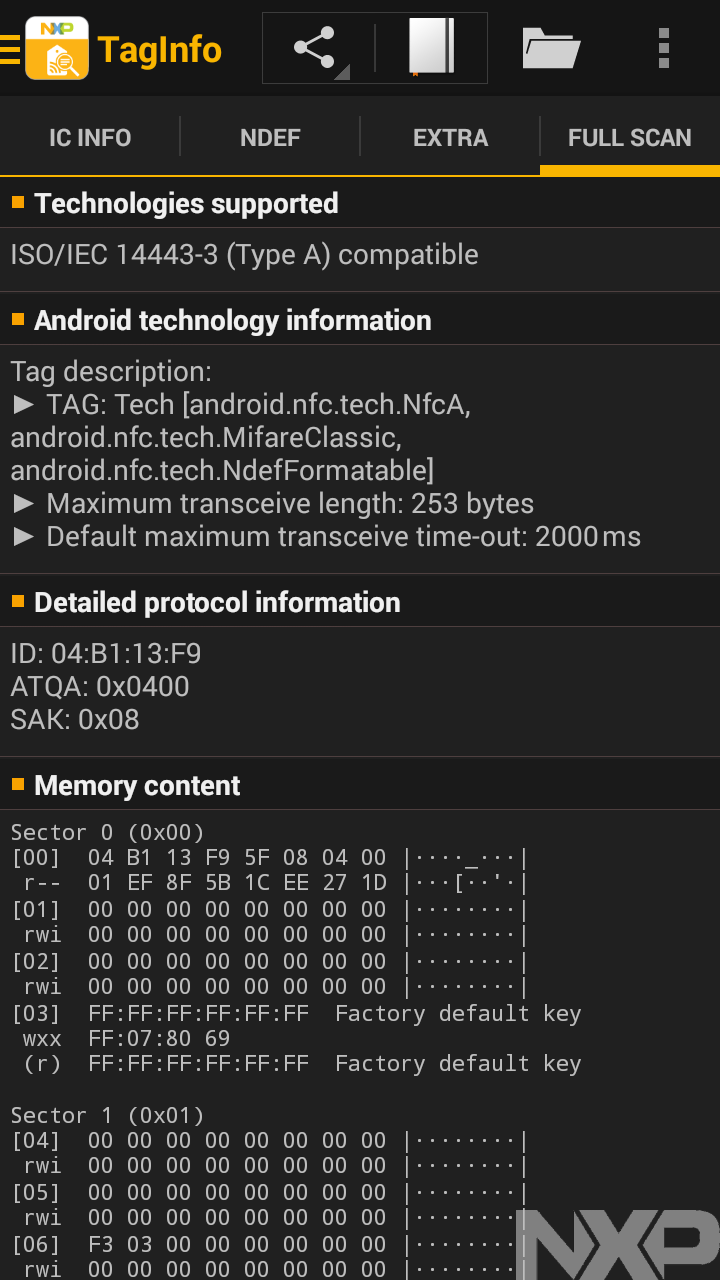
This one is great, the second screen explains a lot of the technical details of the content, like the manufacturer, the model of the headset, the kinds of Bluetooth protocols it supports, and more.
The fourth screen again shows us all the raw memory content that it's getting all that information from, again laid out how it's stored on the tag, in this case in rows of four bytes each, called pages.
[00] * 04:24:52 FA (UID0-UID2, BCC0) [01] * FA:4E:48:80 (UID3-UID6) [02] * 7C 48 FF FF (BCC1, INT, LOCK0-LOCK1) [03] * E1:10:12:0F (OTP0-OTP3) [04] * 01 03 A0 10 |....| [05] * 44 03 4D D2 |D.M.| [06] * 20 2A 61 70 | *ap| [07] * 70 6C 69 63 |plic| [08] * 61 74 69 6F |atio| [09] * 6E 2F 76 6E |n/vn| [0A] * 64 2E 62 6C |d.bl| [0B] * 75 65 74 6F |ueto| [0C] * 6F 74 68 2E |oth.| [0D] * 65 70 2E 6F |ep.o| [0E] * 6F 62 2A 00 |ob*.| [0F] * 34 2A 2D 09 |4*-.| [10] * 18 00 0A 09 |....| [11] * 42 54 20 31 |BT 1| [12] * 30 30 20 4E |00 N| [13] * 43 04 0D 04 |C...| [14] * 04 24 11 03 |.$..| [15] * 08 11 0B 11 |....| [16] * 0C 11 0D 11 |....| [17] * 0E 11 0F 11 |....| [18] * 1E 11 31 11 |..1.| [19] * FE 00 00 00 |....| [1A] * 00 00 00 00 |....| [1B] * 00 00 00 00 |....| [1C] * 00 00 00 00 |....| [1D] * 00 00 00 00 |....| [1E] * 00 00 00 00 |....| [1F] * 00 00 00 00 |....| [20] * 00 00 00 00 |....| [21] * 00 00 00 00 |....| [22] * 00 00 00 00 |....| [23] * 00 00 00 00 |....| [24] * 00 00 00 00 |....| [25] * 00 00 00 00 |....| [26] * 00 00 00 00 |....| [27] * 00 00 00 00 |....| [28] * FF FF -- -- (LOCK2-LOCK3) [29] * 00 00 -- -- (CNT0-CNT1, value: 0) *:locked & blocked, x:locked, +:blocked, .:un(b)locked
Unfortunately, "locked and blocked" here means it's read-only, there's no way to write to this NFC tag and, for example, change what it identifies as for pairing.

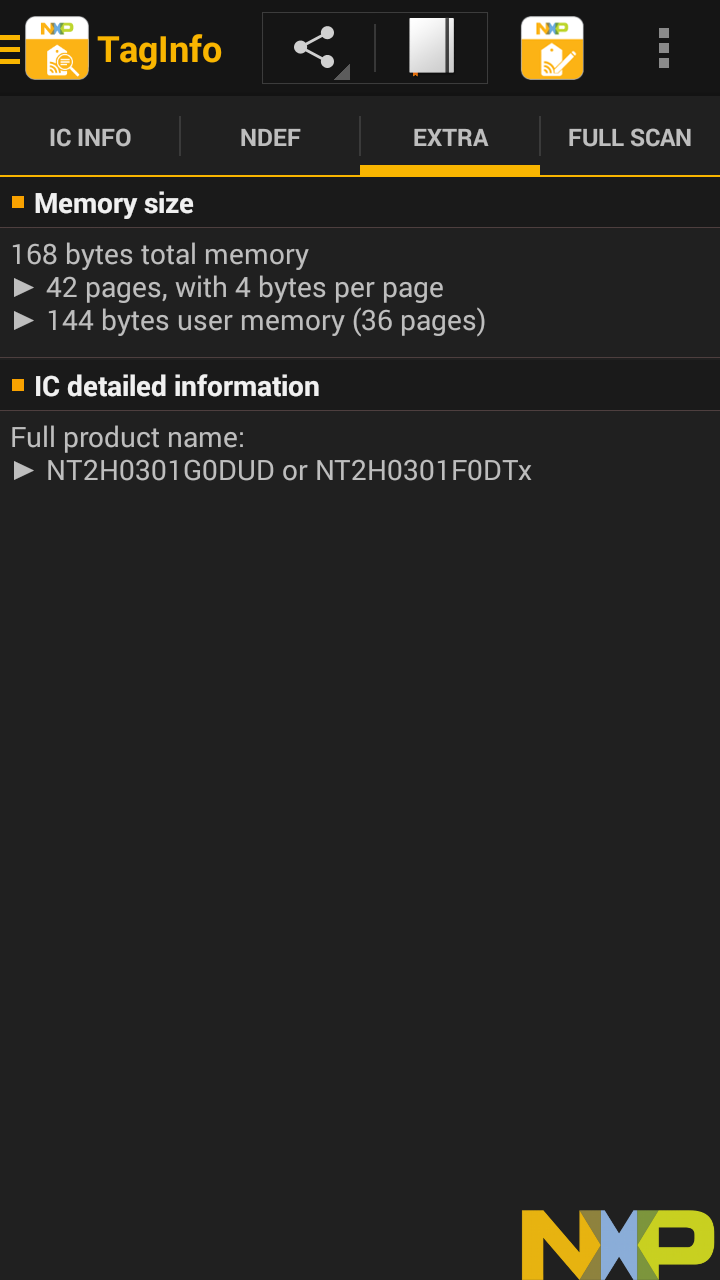
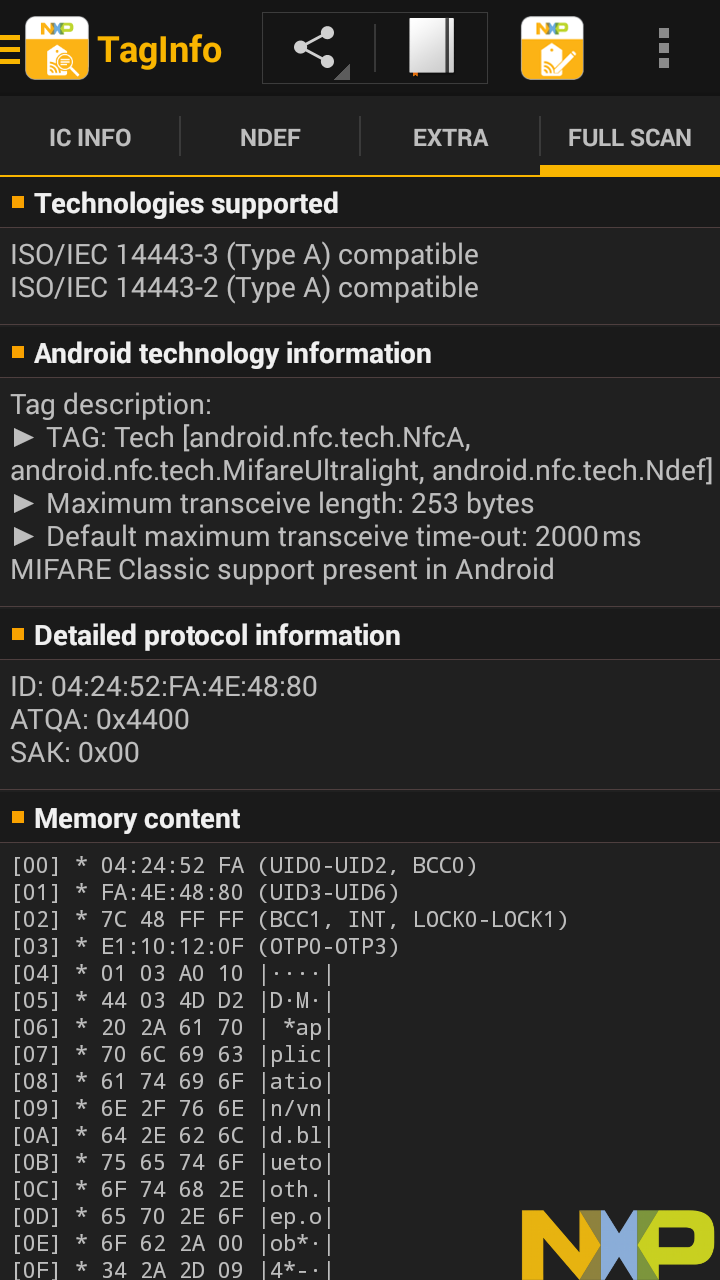
Here is a business card printed by Moo, which embeds an NFC tag to support sharing contact information; sending the user to a URL, app store, or social network profile; or even triggering custom behaviors using IFTTT.
This tag is set up to send a notification to my phone when someone taps it, and then direct them to nfc.toys.
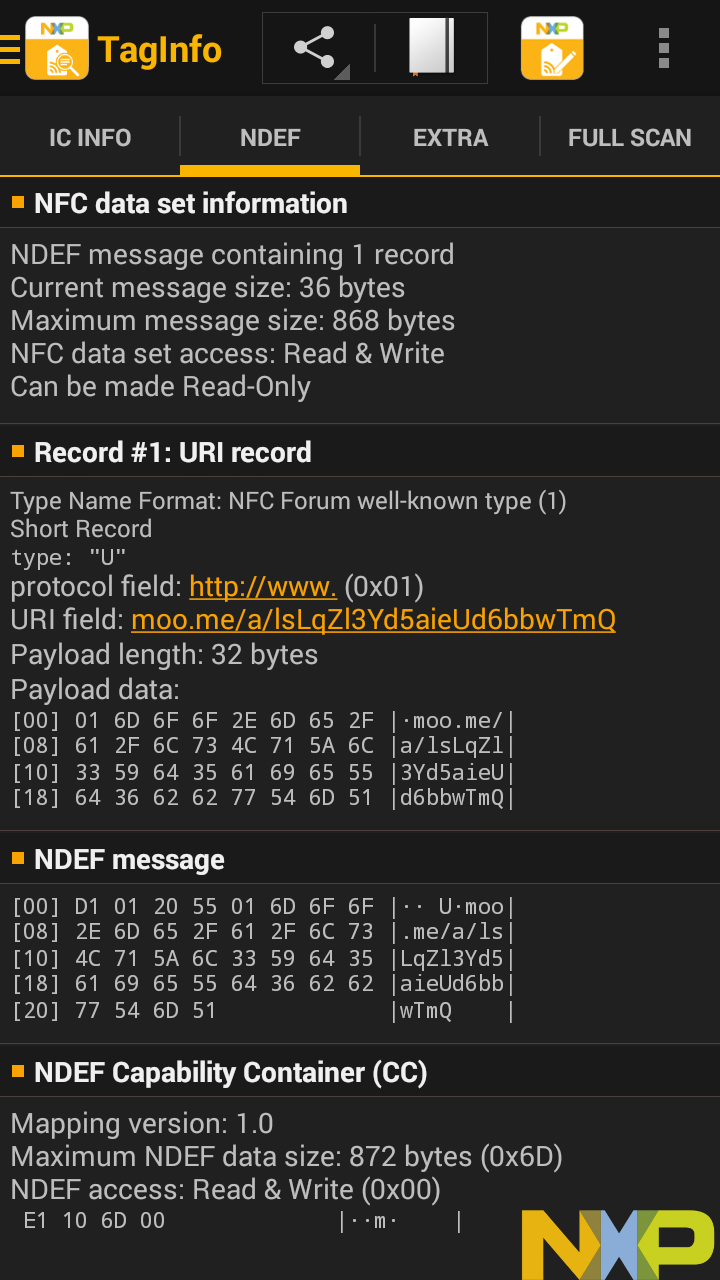
This output is also really detailed. The second screen explains the technical details of the content, in this case the Moo URL that provides all the custom functionality through their online service.
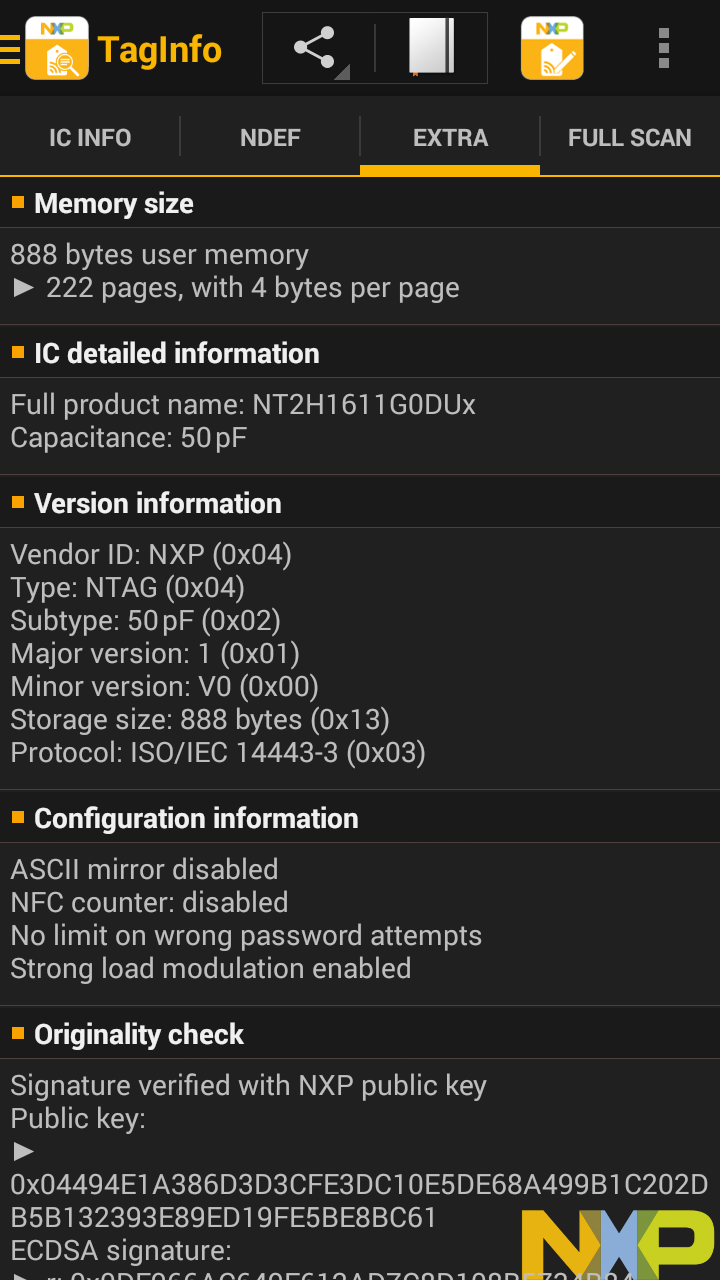
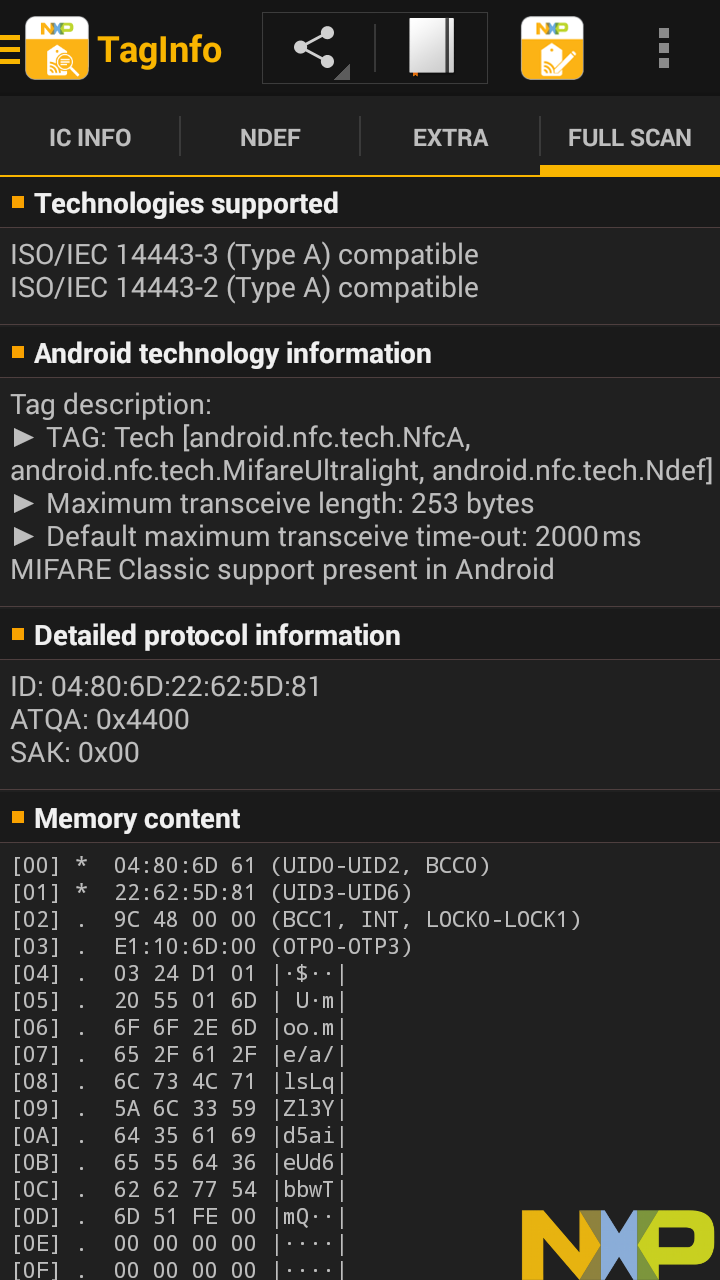
The third screen has detailed information about the NFC tag itself, and the fourth screen again shows us all the raw memory content that it's getting all that information from, again in a pages structure.
[00] * 04:80:6D 61 (UID0-UID2, BCC0) [01] * 22:62:5D:81 (UID3-UID6) [02] . 9C 48 00 00 (BCC1, INT, LOCK0-LOCK1) [03] . E1:10:6D:00 (OTP0-OTP3) [04] . 03 24 D1 01 |.$..| [05] . 20 55 01 6D | U.m| [06] . 6F 6F 2E 6D |oo.m| [07] . 65 2F 61 2F |e/a/| [08] . 6C 73 4C 71 |lsLq| [09] . 5A 6C 33 59 |Zl3Y| [0A] . 64 35 61 69 |d5ai| [0B] . 65 55 64 36 |eUd6| [0C] . 62 62 77 54 |bbwT| [0D] . 6D 51 FE 00 |mQ..| [0E] . 00 00 00 00 |....| [0F] . 00 00 00 00 |....| [10] . 00 00 00 00 |....| [11] . 00 00 00 00 |....| [12] . 00 00 00 00 |....| [13] . 00 00 00 00 |....| [14] . 00 00 00 00 |....| [15] . 00 00 00 00 |....| [16] . 00 00 00 00 |....| [17] . 00 00 00 00 |....| [18] . 00 00 00 00 |....| [19] . 00 00 00 00 |....| [1A] . 00 00 00 00 |....| [1B] . 00 00 00 00 |....| [1C] . 00 00 00 00 |....| [1D] . 00 00 00 00 |....| [1E] . 00 00 00 00 |....| [1F] . 00 00 00 00 |....| [20] . 00 00 00 00 |....| [21] . 00 00 00 00 |....| [22] . 00 00 00 00 |....| [23] . 00 00 00 00 |....| [24] . 00 00 00 00 |....| [25] . 00 00 00 00 |....| [26] . 00 00 00 00 |....| [27] . 00 00 00 00 |....| [28] . 00 00 00 00 |....| [29] . 00 00 00 00 |....| [2A] . 00 00 00 00 |....| [2B] . 00 00 00 00 |....| [2C] . 00 00 00 00 |....| [2D] . 00 00 00 00 |....| [2E] . 00 00 00 00 |....| [2F] . 00 00 00 00 |....| [30] . 00 00 00 00 |....| [31] . 00 00 00 00 |....| [32] . 00 00 00 00 |....| [33] . 00 00 00 00 |....| [34] . 00 00 00 00 |....| [35] . 00 00 00 00 |....| [36] . 00 00 00 00 |....| [37] . 00 00 00 00 |....| [38] . 00 00 00 00 |....| [39] . 00 00 00 00 |....| [3A] . 00 00 00 00 |....| [3B] . 00 00 00 00 |....| [3C] . 00 00 00 00 |....| [3D] . 00 00 00 00 |....| [3E] . 00 00 00 00 |....| [3F] . 00 00 00 00 |....| [40] . 00 00 00 00 |....| [41] . 00 00 00 00 |....| [42] . 00 00 00 00 |....| [43] . 00 00 00 00 |....| [44] . 00 00 00 00 |....| [45] . 00 00 00 00 |....| [46] . 00 00 00 00 |....| [47] . 00 00 00 00 |....| [48] . 00 00 00 00 |....| [49] . 00 00 00 00 |....| [4A] . 00 00 00 00 |....| [4B] . 00 00 00 00 |....| [4C] . 00 00 00 00 |....| [4D] . 00 00 00 00 |....| [4E] . 00 00 00 00 |....| [4F] . 00 00 00 00 |....| [50] . 00 00 00 00 |....| [51] . 00 00 00 00 |....| [52] . 00 00 00 00 |....| [53] . 00 00 00 00 |....| [54] . 00 00 00 00 |....| [55] . 00 00 00 00 |....| [56] . 00 00 00 00 |....| [57] . 00 00 00 00 |....| [58] . 00 00 00 00 |....| [59] . 00 00 00 00 |....| [5A] . 00 00 00 00 |....| [5B] . 00 00 00 00 |....| [5C] . 00 00 00 00 |....| [5D] . 00 00 00 00 |....| [5E] . 00 00 00 00 |....| [5F] . 00 00 00 00 |....| [60] . 00 00 00 00 |....| [61] . 00 00 00 00 |....| [62] . 00 00 00 00 |....| [63] . 00 00 00 00 |....| [64] . 00 00 00 00 |....| [65] . 00 00 00 00 |....| [66] . 00 00 00 00 |....| [67] . 00 00 00 00 |....| [68] . 00 00 00 00 |....| [69] . 00 00 00 00 |....| [6A] . 00 00 00 00 |....| [6B] . 00 00 00 00 |....| [6C] . 00 00 00 00 |....| [6D] . 00 00 00 00 |....| [6E] . 00 00 00 00 |....| [6F] . 00 00 00 00 |....| [70] . 00 00 00 00 |....| [71] . 00 00 00 00 |....| [72] . 00 00 00 00 |....| [73] . 00 00 00 00 |....| [74] . 00 00 00 00 |....| [75] . 00 00 00 00 |....| [76] . 00 00 00 00 |....| [77] . 00 00 00 00 |....| [78] . 00 00 00 00 |....| [79] . 00 00 00 00 |....| [7A] . 00 00 00 00 |....| [7B] . 00 00 00 00 |....| [7C] . 00 00 00 00 |....| [7D] . 00 00 00 00 |....| [7E] . 00 00 00 00 |....| [7F] . 00 00 00 00 |....| [80] . 00 00 00 00 |....| [81] . 00 00 00 00 |....| [82] . 00 00 00 00 |....| [83] . 00 00 00 00 |....| [84] . 00 00 00 00 |....| [85] . 00 00 00 00 |....| [86] . 00 00 00 00 |....| [87] . 00 00 00 00 |....| [88] . 00 00 00 00 |....| [89] . 00 00 00 00 |....| [8A] . 00 00 00 00 |....| [8B] . 00 00 00 00 |....| [8C] . 00 00 00 00 |....| [8D] . 00 00 00 00 |....| [8E] . 00 00 00 00 |....| [8F] . 00 00 00 00 |....| [90] . 00 00 00 00 |....| [91] . 00 00 00 00 |....| [92] . 00 00 00 00 |....| [93] . 00 00 00 00 |....| [94] . 00 00 00 00 |....| [95] . 00 00 00 00 |....| [96] . 00 00 00 00 |....| [97] . 00 00 00 00 |....| [98] . 00 00 00 00 |....| [99] . 00 00 00 00 |....| [9A] . 00 00 00 00 |....| [9B] . 00 00 00 00 |....| [9C] . 00 00 00 00 |....| [9D] . 00 00 00 00 |....| [9E] . 00 00 00 00 |....| [9F] . 00 00 00 00 |....| [A0] . 00 00 00 00 |....| [A1] . 00 00 00 00 |....| [A2] . 00 00 00 00 |....| [A3] . 00 00 00 00 |....| [A4] . 00 00 00 00 |....| [A5] . 00 00 00 00 |....| [A6] . 00 00 00 00 |....| [A7] . 00 00 00 00 |....| [A8] . 00 00 00 00 |....| [A9] . 00 00 00 00 |....| [AA] . 00 00 00 00 |....| [AB] . 00 00 00 00 |....| [AC] . 00 00 00 00 |....| [AD] . 00 00 00 00 |....| [AE] . 00 00 00 00 |....| [AF] . 00 00 00 00 |....| [B0] . 00 00 00 00 |....| [B1] . 00 00 00 00 |....| [B2] . 00 00 00 00 |....| [B3] . 00 00 00 00 |....| [B4] . 00 00 00 00 |....| [B5] . 00 00 00 00 |....| [B6] . 00 00 00 00 |....| [B7] . 00 00 00 00 |....| [B8] . 00 00 00 00 |....| [B9] . 00 00 00 00 |....| [BA] . 00 00 00 00 |....| [BB] . 00 00 00 00 |....| [BC] . 00 00 00 00 |....| [BD] . 00 00 00 00 |....| [BE] . 00 00 00 00 |....| [BF] . 00 00 00 00 |....| [C0] . 00 00 00 00 |....| [C1] . 00 00 00 00 |....| [C2] . 00 00 00 00 |....| [C3] . 00 00 00 00 |....| [C4] . 00 00 00 00 |....| [C5] . 00 00 00 00 |....| [C6] . 00 00 00 00 |....| [C7] . 00 00 00 00 |....| [C8] . 00 00 00 00 |....| [C9] . 00 00 00 00 |....| [CA] . 00 00 00 00 |....| [CB] . 00 00 00 00 |....| [CC] . 00 00 00 00 |....| [CD] . 00 00 00 00 |....| [CE] . 00 00 00 00 |....| [CF] . 00 00 00 00 |....| [D0] . 00 00 00 00 |....| [D1] . 00 00 00 00 |....| [D2] . 00 00 00 00 |....| [D3] . 00 00 00 00 |....| [D4] . 00 00 00 00 |....| [D5] . 00 00 00 00 |....| [D6] . 00 00 00 00 |....| [D7] . 00 00 00 00 |....| [D8] . 00 00 00 00 |....| [D9] . 00 00 00 00 |....| [DA] . 00 00 00 00 |....| [DB] . 00 00 00 00 |....| [DC] . 00 00 00 00 |....| [DD] . 00 00 00 00 |....| [DE] . 00 00 00 00 |....| [DF] . 00 00 00 00 |....| [E0] . 00 00 00 00 |....| [E1] . 00 00 00 00 |....| [E2] . 00 00 00 BD (LOCK2-LOCK4, CHK) [E3] . 04 00 00 FF (CFG, MIRROR, AUTH0) [E4] . 00 05 -- -- (ACCESS) [E5] +P FF FF FF FF (PWD0-PWD3) [E6] +P 00 00 -- -- (PACK0-PACK1) *:locked & blocked, x:locked, +:blocked, .:un(b)locked, ?:unknown r:readable (write-protected), p:password protected, -:write-only P:password protected write-only
This entire business card appears writable, meaning we could put anything we want on it, even replacing Moo's online service with our own.
Skylanders and MIFARE


Those other NFC tags show me memory contents and the layout of data on the tag, but the TNP3xxx in the Skylander figure doesn't show me anything. But, we know that it has memory, the third tab says so. So, what's up?
To figure it out, let's use that elite hacking technique called, go poking around the internet.
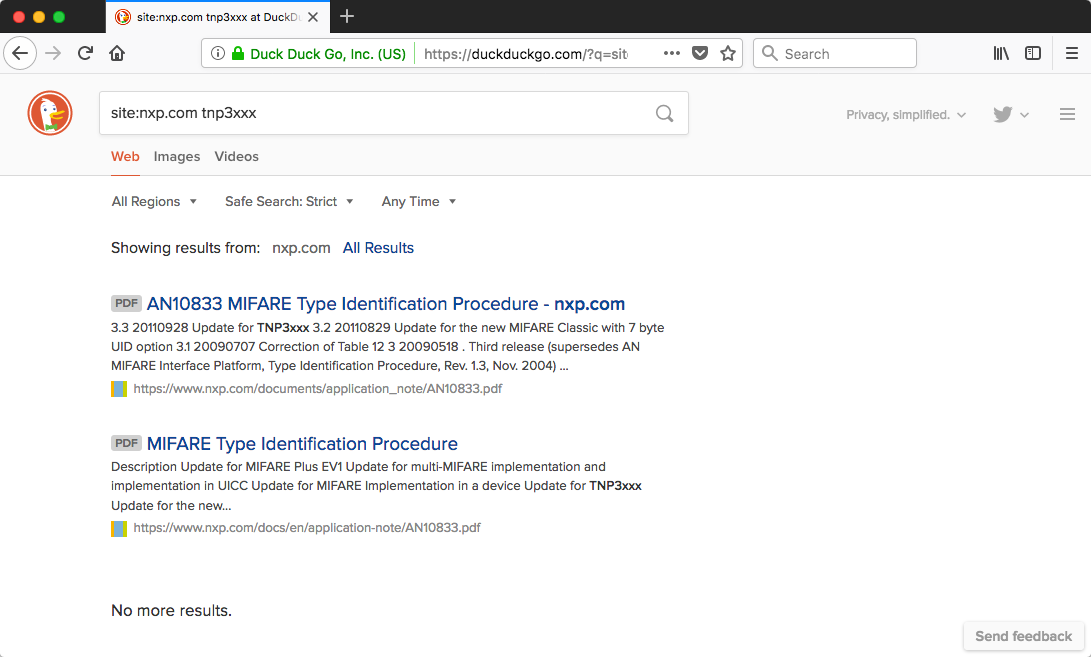
If we search NXP's web site for "tnp3xxx",

we find it in this PDF describing ways to identify NXP MIFARE tags, so it's a MIFARE tag. Curiously, it doesn't have any other information,
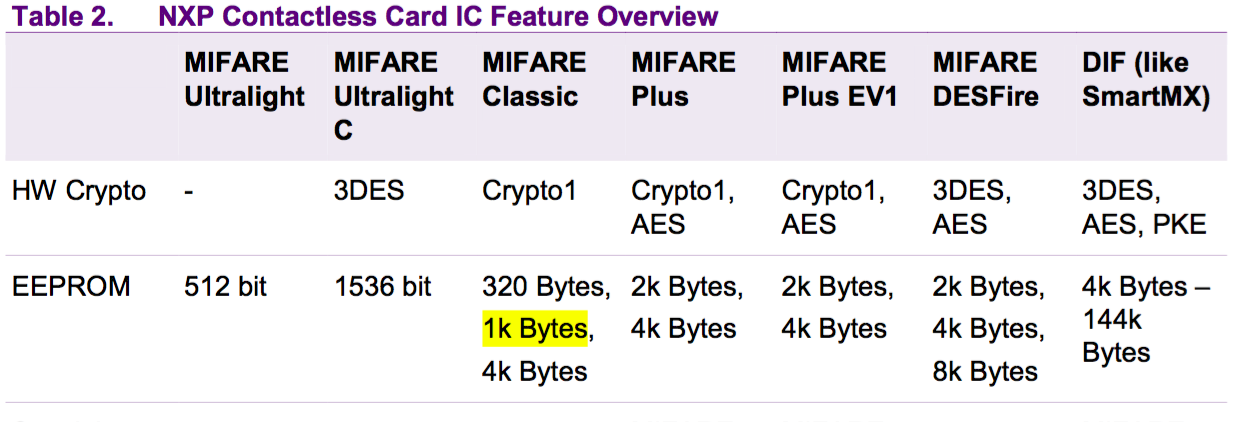
but Table 2 describes another MIFARE tag with 1kB memory, the MIFARE Classic.
Wikipedia describes the MIFARE Classic's memory size as so:
The MIFARE Classic 1K offers 1024 bytes of data storage, split into 16 sectors; each sector is protected by two different keys, called A and B. Each key can be programmed to allow operations such as reading, writing, increasing value blocks, etc.
That matches what the third screenshot from NXP TagInfo told us, so maybe the TNP3xxx is a MIFARE Classic-compatible tag, even if TagInfo pretends to not know what it is.
Wikipedia also says this:
MIFARE Classic encryption has been compromised; see below for details.
As a common type of NFC tag, MIFARE Classic is pretty well-explored from a security standpoint.
If TNP3xxx is a MIFARE Classic-derivative, could it be vulnerable to the same exploits that MIFARE Classic tags are, allowing us access to the tag?

libnfc hardware

That's as far as we can get on a Skylanders toy with an Android phone, so it's time to upgrade to the second of three standard tools I'll be discussing: dedicated NFC reader hardware plugged into your computer.
We want to look for hardware that's compatible with the libnfc open-source library, which supports a select range of NFC reader chips on Linux, Mac, and even Windows with some futzing.
We want libnfc-compatible hardware, because a lot of the dedicated NFC readers you'll find are Windows-only, or only expose low-level communication functions, requiring more complex, technical programming.
There are higher-level, easier-to-use libraries in various languages which use libnfc under the hood, and so it provides security researchers and hobbyists alike with a standard platform.
You can find a libnfc-supported NFC reader for around $50.
MIFARE Classic
In addition to a libnfc-supported NFC reader, plugged into our Mac or Linux computer, we'll also need to already know, or be comfortable figuring out, how to compile software ourselves, but we won't need to write anything new.
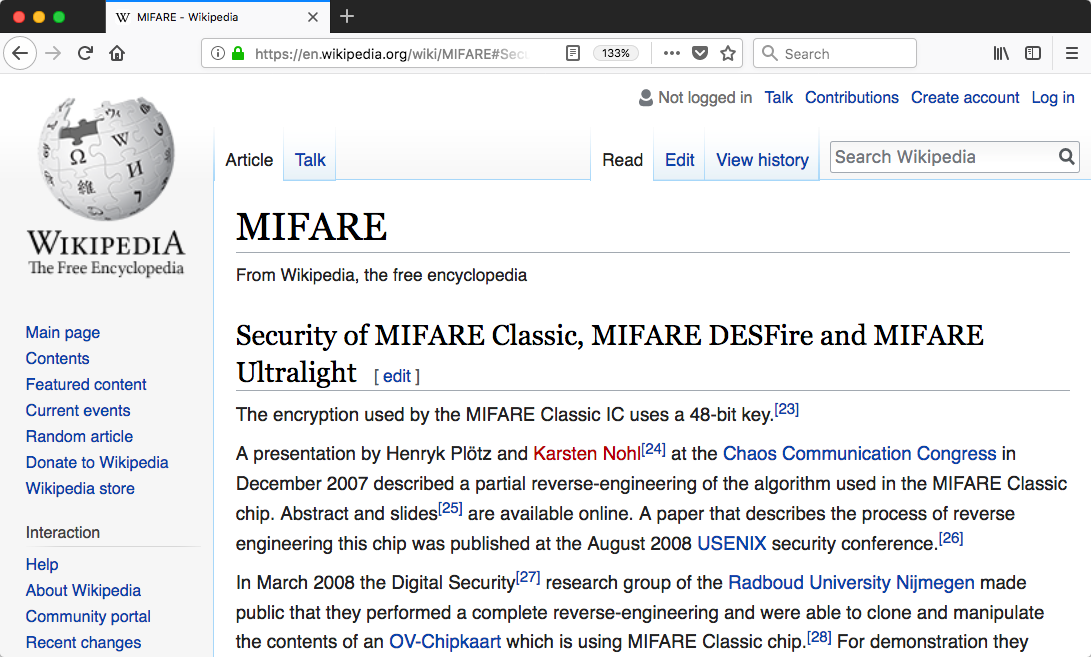
Wikipedia describes something like nine different papers and presentations, starting from 2007, which provide various attacks on and compromises to MIFARE Classic tags. In addition, NXP released updated, so-called "hardened" versions of MIFARE tags "in and around 2011". In exploring this Ninjini toy, we're really just taking the next steps in a long line of scholarship.

This Ninjini toy is from 2012, the Giants line. I use it as an example because it's bigger, and it lights up, but if it's a MIFARE Classic in disguise, we're going to have to use a compromise that works against the hardened version of the tag, like the one from this paper, published in 2015,
Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards
Carlo Meijer, Roel Verdult
which finally led NXP to tell people to stop using them.
Furthermore, NXP does not recommend to design in MIFARE® Classic in any security relevant application.
All you need, is one known key. What's a key?
Remember that payment card from earlier, and its memory layout?
Sector 1 (0x01)
[04] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[05] rwi 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[06] rwi F3 03 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[07] wxx XX:XX:XX:XX:XX:XX FF:07:80 69 FF:FF:FF:FF:FF:FF
(unknown key) Factory default key (readable)
This is the same as how a MIFARE Classic tag is laid out, in sixteen sectors, numbered zero through fifteen:
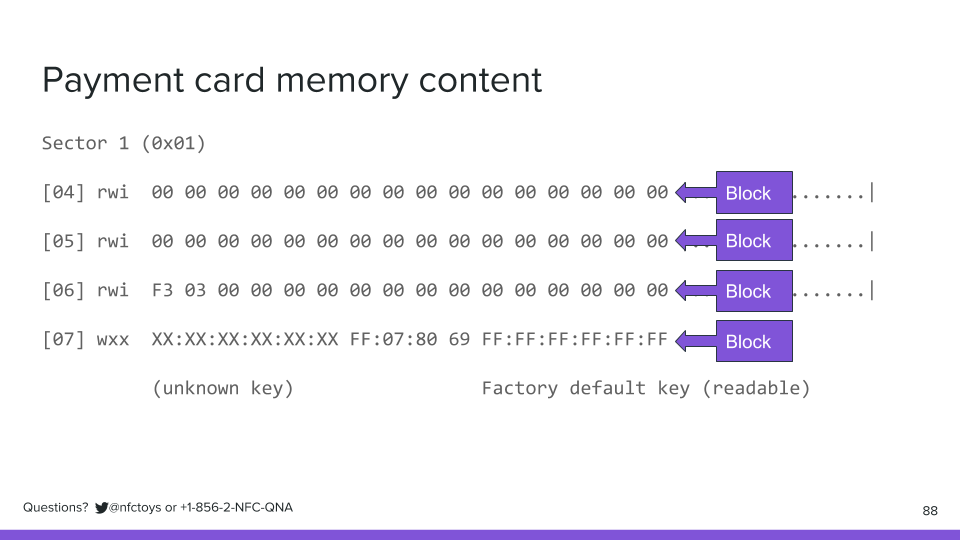
Each of those rows in each sector is called a block. Each block can store sixteen bytes. Sixteen bytes, times four blocks, times sixteen sectors, is 1K of storage:
The last block in each sector stores two passwords, called key A and key B, and access bits in between them, which define which of the keys can read or write the blocks, as well as read or write the other key:
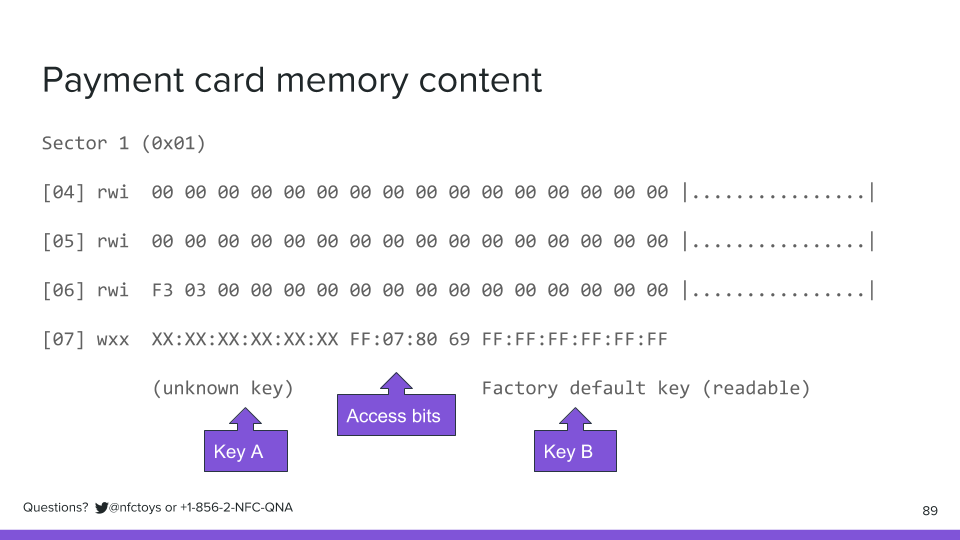
In this sector from the payment card, the first password, key A, is hidden, unknown, X'd out, which probably means you need it to update the dollar value stored on the tag. The second password, key B, is the factory default key, and it's readable, which means we can see it, and probably also means we can only use it to see what data is on the tag, but not change it.
Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards
Carlo Meijer, Roel Verdult
Sixteen sectors, a key A and key B each, means there can be up to thirty-two passwords you need to uncover to get access to a completely locked-down 1k MIFARE Classic tag, but what this paper tells us, is we only need to know one, and due to vulnerabilities in the tag's logic, it can figure out the rest from there.
Knowing one in advance is not as difficult a task as it might seem like. Obviously we already know one for this payment card, maybe the TNP3xxx has a similar situation. We could search documentation and source code for common MIFARE keys and try each one of them against the key A and key B for every sector, and, spoiler alert, it'll eventually work, you'll eventually find one.
But, this is 2018, and you have slightly newer information available to you than I did when I did that myself back in 2014. Let's head back to the internet to find it.
A single key
So we're looking for a known key for a Skylanders toy, and some not-so-creative searching nets us an interesting paper,
Comprehensive security analyses of a toys-to-life game and possible countermeasures
a Masters thesis by Kevin Valk.
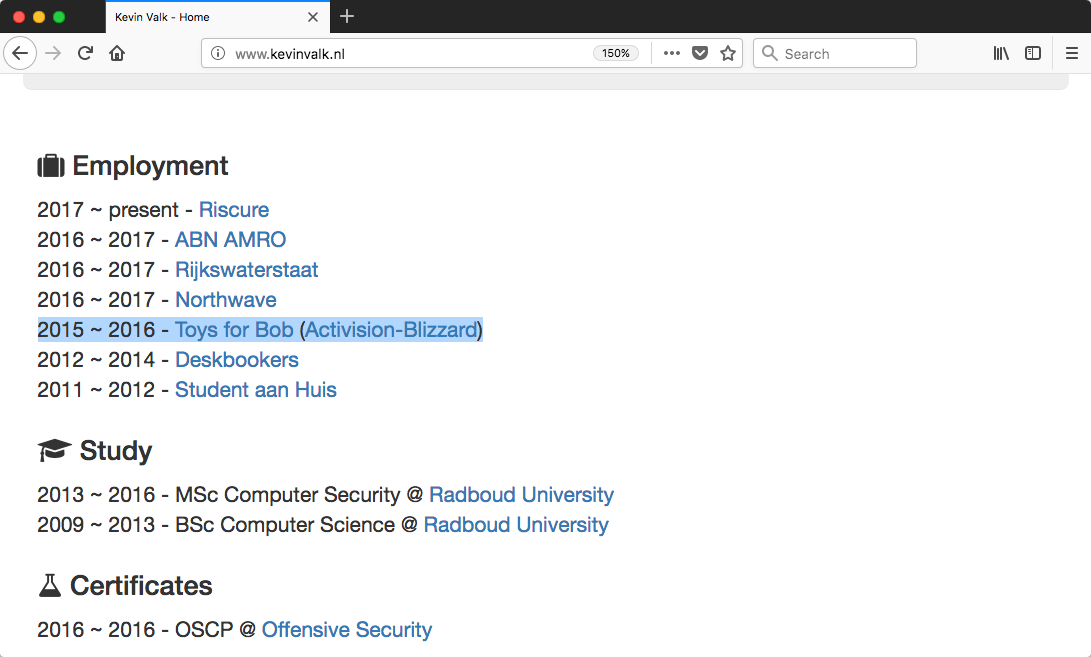
and when you find the author's home page, you also find the fact that he worked with Toys for Bob, developers of Skylanders, for a year.
The thesis never says Skylanders by name, but knowing what we know now, it's easy to recognize that's what it's about. And, it contains exactly what we're looking for:
The collected keys showed that the first sector always has the same static key, but all other sector keys were seemingly random.
and:
Sector zero key is static and by using the sector one key all other sector keys can be derived.
The first key, key A, in every toy is the same. And what does the paper say the first key is?
4B0B20107CCB
Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards
Comprehensive security analyses of a toys-to-life game and possible countermeasures
4B0B20107CCB
Okay, thanks to two research papers, we have a known key, and we have an attack vector, now we need software to run it that works with libnfc.
Let's look for Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards libnfc,
and a little ways down on the page, we have an implementation of the paper's algorithms suitable for use with libnfc, by security researcher Aram Verstegen.
If you compile and run their libnfc_crypto1_crack program with a Giants figure, you'll get:
./libnfc_crypto1_crack 4b0b20107ccb 0 A 4 A
Found tag with uid 7663a4ac, collecting nonces for key A of block 4 (sector 1) using known key A 4b0b20107ccb for block 0 (sector 0)
Collected 2211 nonces... leftover complexity 1922878139392 (~2^40.81) - press enter to start brute-force phase
...
Collected 3088 nonces... leftover complexity 1922878139392 (~2^40.81) - initializing brute-force phase...
Starting 4 threads to test 1922878139392 states using 128-way bitslicing
Cracking... 42.25%
Found key: 5ac1b0c34b55
Tested 812351825060 states
That's a valid key for block 4 (sector 1), and you can repeat that for a block in each of the remaining sectors.
Just to make sure, let's try it with an even later model Trap Team figure, and we get:
./libnfc_crypto1_crack 4b0b20107ccb 0 A 9 A
Found tag with uid 6f4dd098, collecting nonces for key A of block 9 (sector 2) using known key A 4b0b20107ccb for block 0 (sector 0)
Collected 1691 nonces... leftover complexity 290639890944 (~2^38.08) - initializing brute-force phase...
Starting 4 threads to test 290639890944 states using 128-way bitslicing
Cracking... 66.08%
Found key: 1d0d8836e897
Tested 192051123140 states
That's a valid key for block 9 (sector 2), and you can repeat that for a block in each of the remaining sectors.
With this, you can get keys A for every Skylanders toy.
You can then plug these into any libnfc MIFARE reading app, or into MIFARE reading apps on your supported Android phone, assuming the apps recognize the Skylanders as MIFARE Classic tags, and see the full contents of the toy. That looks like this:
048b9f382881010fc427000000000012
6d00000070dccb6ed34d00000612f2fe
00000000000000000000000000000000
4b0b20107ccb0f0f0f69000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
edb9a575cc357f0f0869000000000000
5b00e0d3a691ea9d6a93c93348c35d5f
b893ce40958a66d3faee5c5a8cb15116
3982b1519ae73c4c2e83f19c8545c2c8
cbd471261bf67f0f0869000000000000
0f5dc22225ac4cc829f13c9bb5b945a6
70574d5c8be3164624e04abb9225c0aa
b4fb860161020cd3a69ef8ec2b49db23
58e29b8ff0177f0f0869000000000000
78330690ea993234f430bd9ffbbe4ca2
43968ac84bb0b4099a25a49732a5f831
4d0ab7ac143273852a7797097d402024
143833285e907f0f0869000000000000
2f0b587954b1d9359c3e839e24084a8d
3e9b2242b05332dccd47743fb94ff797
00000000000000000000000000000000
870ed981b5717f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
a1630dd262b27f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
3255e77b89537f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
aae1b634d45c7f0f0869000000000000
5c0ec67a608e97a1bc3253f820b5549c
407c1fdf76b97cbf9f9df6a6251ea3a0
d3cc12b4374fa085a9c82460d38b3484
39d75c9d3fbd7f0f0869000000000000
a643e3ba6683cee88aebb7d5f0716bd2
d1872d944c1e9c11a1a5f9038db96967
ca7f32c64c0ab792e695ccd918a9a58a
1fba88cee87e7f0f0869000000000000
f3268969aad925141a6f476cc01802ae
63873a385286acca7e91c3582823d675
cfbc77e45fb944fb7d3c5ee4aaac50ef
8c8c6267039f7f0f0869000000000000
7d910ce264ad63270e6bb427e1f51ffb
8f7cc6b94dc46470c0fecede3fb8a0b0
00000000000000000000000000000000
c056cac0ad187f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
5360206946f97f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
750df43a913a7f0f0869000000000000
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
e63b1e937adb7f0f0869000000000000
(This output is just like NXP TagInfo's rendering of the payment card, just all smushed together.)
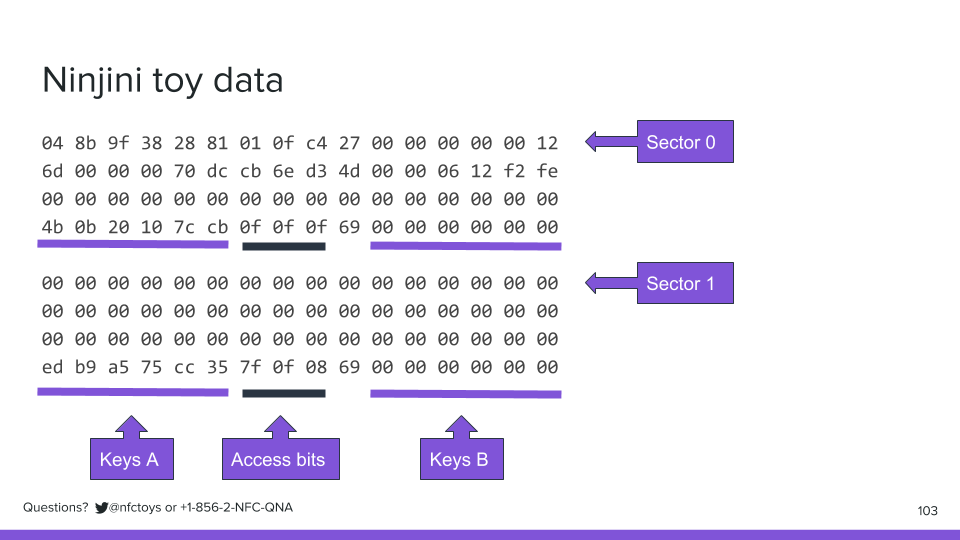
Just like in the payment card, you can see the access bits on every fourth line.
Sector zero, blocks 0-3, has the access bits 0f0f0f.
Sector 1, blocks 4-7, and every sector after that, have the access bits 7f0f08. If we look in NXP's MIFARE Classic documentation, we see we have to turn it into binary, and we'll learn this:
Sector 0, the first four blocks on the toy, is completely read only.
Every other sector is writable by its key A. We can't ever read each key A, so we always have to know them in advance. Key B is all zeros, which is a really common password, but it can't do anything, so all it's good for is being used to exploit other keys.
There's more, but that's enough for us to know that we can completely own any given Skylanders toy. With a method to obtain all the keys A, we have full read and write access to every available block, that's fifteen sectors, three writable blocks of 16 bytes each,
for a total of 720 bytes we can write anything we want to.
There's one more thing, going back to that quote we pulled from the Valk thesis.
Sector zero key is static and by using the sector one key all other sector keys can be derived.
For the toys to work as they do, across multiple platforms, and offline, with every key A on every toy being different, there has to be some formula or math that sets them, that the portal or game knows, that has to be based on some fixed, immutable information about the character, like the content in sector zero.
So, how do you figure out what that formula is?
Well, if you're like me, or like the security researchers who eventually figured it out, you buy and crack a lot more toys.
As RFID and security researchers discovered across 2014 and 2015, if you collect enough keys, and do some math, you can see patterns in how each sector's keys relate to each other, and come up with more than one method to generate the keys.
While certainly not obvious, it feels as if there is some sort of shifting to the left happening. Moreover, when doing an exclusive or operation between a key and the key that follows (K[i] ⊕ K[i + 1]), it becomes apparent that there is indeed some pattern, this can be seen in Table 4.
It turns out that K[i] ⊕ K[i + 1] for i in range [2, 16) has the same outcome for every NUID. Sector zero key is static and by using the sector one key all other sector keys can be derived. Verification of this hypothesis is shown in Table 5 and holds for all tested NUIDs. However, the sector one key is the only exception as K[1] = K[0] ⊕ (K[0] ⊕ K[1]) does not hold across different NUIDs.
Valk's thesis even included the fact that patterns in the keys could be discovered, documenting that there were patterns, but he did not go so far as to document what the patterns meant.
New interoperability for Skylanders
So, today, I present the first, public, clean room description of an algorithm to generate the keys A for all Skylanders figures released to date. I'm publishing this to support new interoperability of Activision Skylanders NFC toys.
The key A for sector 0 is always the 6-byte (12-character) hexadecimal representation of the integer computed by the multiplication of the three prime numbers 73 and 2017 and 560,381,651
For all other sectors, let a big-endian, most-significant-bit first, 48-bit CRC computation use the ECMA-182 polynomial of
0x42f0e1eba9ea3693, and not be reflected or reversed or have a final register XOR value; this is equivalent to a CRC64-ECMA-182 with left shift, MSB check and remainder trim reduced from 64 to 48 bitsLet the initial value of the CRC48 register be the value of the integer computed by the multiplication of the five prime numbers 2 and 2 and 3 and 1103 and 12,868,356,821
Compute the CRC48 of the 5 bytes encoded by the 10-character hexadecimal concatenation of the UID and the sector number in hexadecimal
The key A for that sector is 6 bytes, represented in hexadecimal as 12 characters: the result of the CRC48 with the hexadecimal bytes' order reversed
By knowing an algorithm used to set the read/write passwords (keys A), we can interoperably read/write our own data to a Skylanders NFC toy, using our own NFC hardware and software, without tedious manual cracking on a per-toy basis.
On nfc.toys, you'll find a video showing me writing custom data using a Mac with an off-the-shelf USB NFC reader, and reading that custom data back out with a Raspberry Pi, using an off-the-shelf, NFC add-on.
You'll also find a sample implementation of this algorithm in Python 2.
Disney Infinity

We're set for Skylanders. Let's talk about Disney Infinity next.

A show of hands, who has kids who were into Disney Infinity?
A show of hands, who was personally into Disney Infinity,
and was devastated, as I was, when they canceled the series?
For everyone else, Disney Infinity was Disney's entry into the toys-to-life genre, launched in 2013.

As in Skylanders, the toy you place on their base is the character you play as in game. Unlike Skylanders, which is all mostly original IP,

Disney Infinity let you play with characters from many different Disney properties, all together in an open-world sandbox environment called the Toy Box.

There were also separate story-based environments for specific franchises and characters, such as a Pirates of the Caribbean play set,

various Pixar play sets,

various Marvel play sets,

and various Star Wars play sets. Sequels were released in 2014 and 2015, resulting in over 300 NFC toys, between figures and accessories.

This is a "Kanan Jarrus" figure from Disney Infinity as seen in NXP TagInfo.
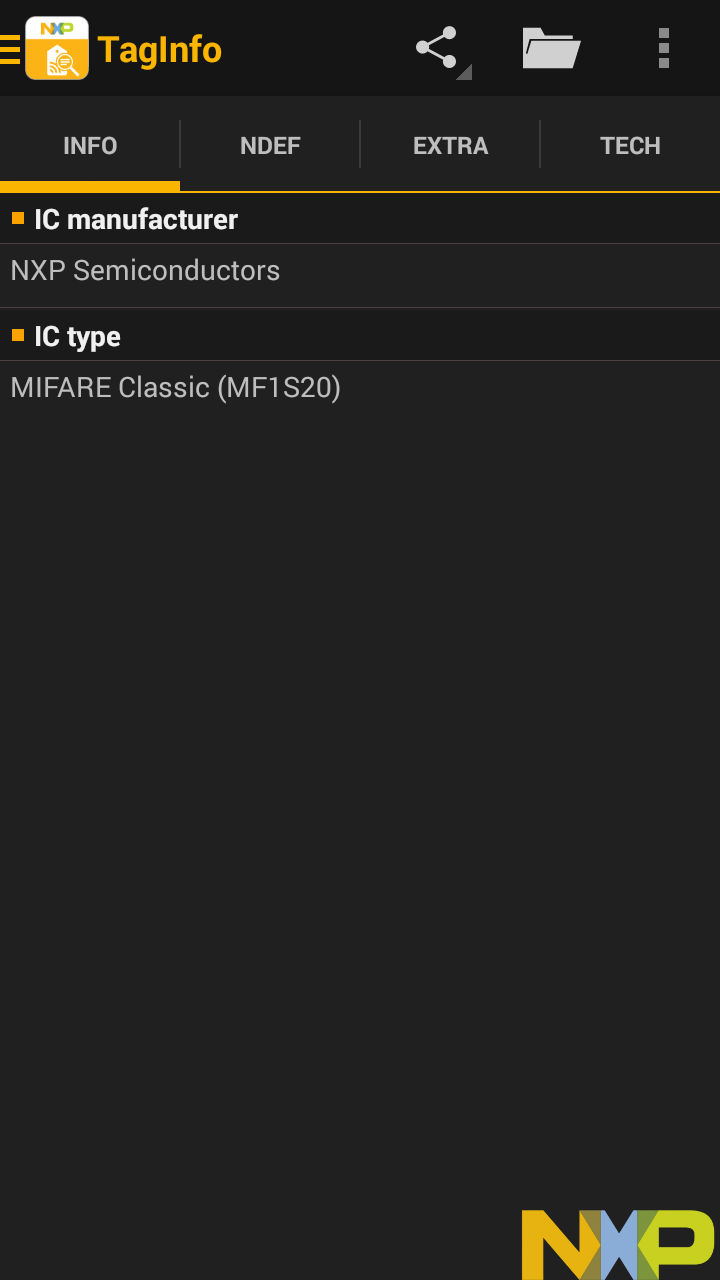
Here, we can see it's an NXP tag, too, specifically a MIFARE Classic (MF1S20) tag.

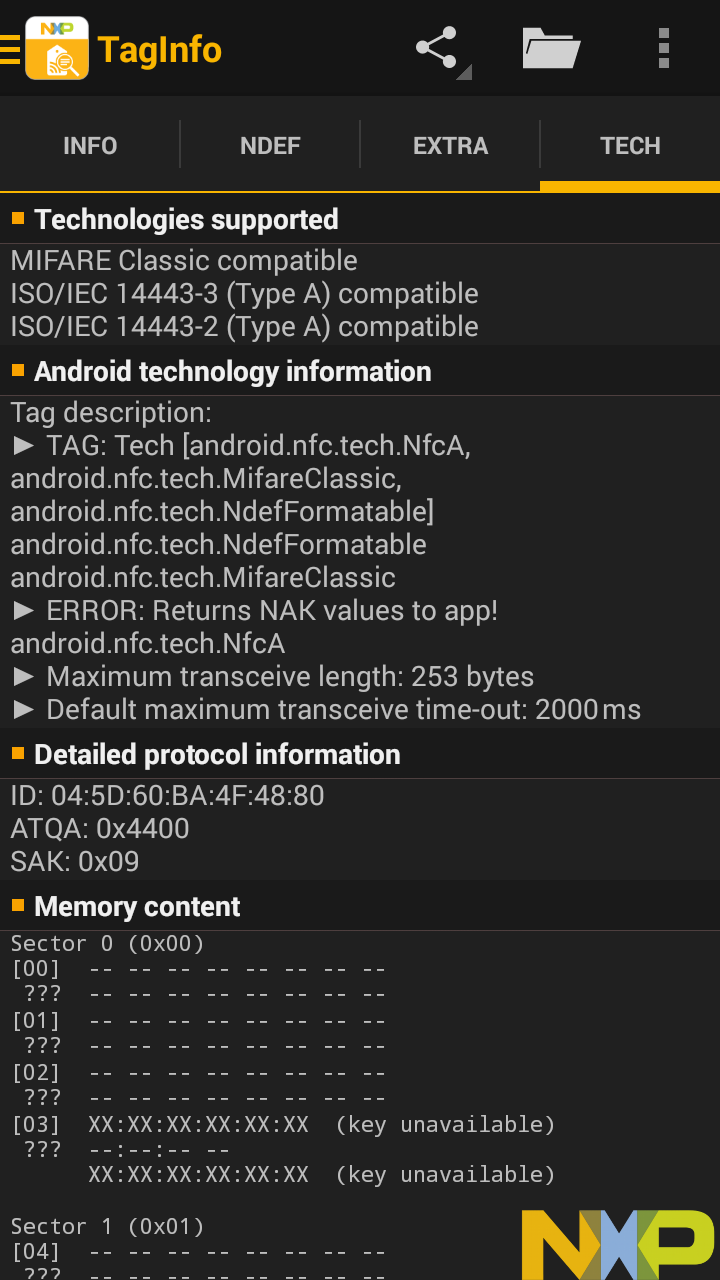
We can see there's 320 bytes total on the tag. We can see its ID, ATQA, and SAK.
And we can also see memory content!
Sector 0 (0x00)
[00] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[01] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[02] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[03] ??? XX:XX:XX:XX:XX:XX --:--:-- -- XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 1 (0x01)
[04] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[05] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[06] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[07] ??? XX:XX:XX:XX:XX:XX --:--:-- -- XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 2 (0x02)
[08] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[09] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[0A] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[0B] ??? XX:XX:XX:XX:XX:XX --:--:-- -- XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 3 (0x03)
[0C] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[0D] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[0E] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[0F] ??? XX:XX:XX:XX:XX:XX --:--:-- -- XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
Sector 4 (0x04)
[10] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[11] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[12] ??? -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
[13] ??? XX:XX:XX:XX:XX:XX --:--:-- -- XX:XX:XX:XX:XX:XX
(unknown key) (unknown key)
r/R=read, w/W=write, i/I=increment,
d=decr/transfer/restore, x=r+w, X=R+W
data block: r/w/i/d:key A|B, R/W/I:key B only,
I/i implies d, *=value block
trailer (order: key A, AC, key B): r/w:key A,
W:key B, R:key A|B, (r)=readable key
AC: W implies R+r, R implies r
It's all crossed out, and reports "unknown key." It's like that all the way down, for all 320 bytes. But, at least we can see the structure of the storage on the tag, which we couldn't for the Skylander.
We're less fortunate working with Disney Infinity figures. None of the ten keys are standard keys, so any exploit that relies on knowing a key won't work. In addition, Disney Infinity came out in 2013, well after NXP hardened the MIFARE Classic.
Proxmark

To get into these figures, we're going to have upgrade to the third of three standard tools I'll be discussing: specialized RFID testing equipment.
Phones and libnfc-compatible hardware can get you far, but to figure out NFC tags that are password-protected and not exploitable, you'll need to be able to listen in on the wireless communication between the tag and the reader, and that means using more serious hardware.
The Proxmark was an open source design for RFID test equipment, providing high-end functionality at a much lower price point than commercial test equipment. Because NFC is a subset of RFID, it works for NFC toys, too. As specialized RFID test equipment, though, it also requires a more thorough understanding of RFID in general.

Depending on where you get it from,
a new Proxmark3 will run $200-400.
Their community is very active, and it's possible someone has already figured out the tag you're looking at, although you'll need technical expertise to translate something that works on the Proxmark to something that works for a general-purpose NFC reader.
Disney Infinity and Proxmark
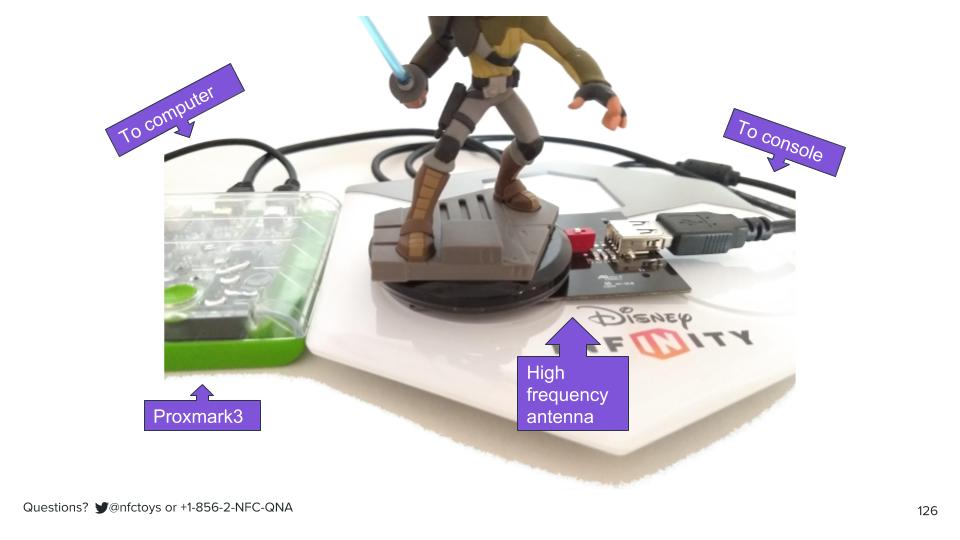
A Proxmark3 will let us place our own antenna right up against the antenna in the NFC reader and the antenna in the NFC toy, and listen in on the communication between the figure and the base. Remember, all of these data transfers are happening wirelessly, over the air, even though the toy and the base are just a few millimeters of plastic apart. If we listen in, we can get the keys.

Unfortunately, that also means we're going to need the video game,

and a console to play it on, since we need the conversation to happen. It was possible to get into a Skylanders figure with just a toy, a thesis, and a research paper, but not so for figuring out Disney Infinity. We'll talk about how that affects our risk later.
hf mf nested 0 4 A 6dd747e86975
Testing known keys. Sector count=5
nested...
Time in nested: 1.825 (inf sec per key)
-----------------------------------------------
Iterations count: 0
|---|----------------|---|----------------|---|
|sec|key A |res|key B |res|
|---|----------------|---|----------------|---|
|000| 6dd747e86975 | 1 | 6dd747e86975 | 1 |
|001| 6dd747e86975 | 1 | 6dd747e86975 | 1 |
|002| 6dd747e86975 | 1 | 6dd747e86975 | 1 |
|003| 6dd747e86975 | 1 | 6dd747e86975 | 1 |
|004| 6dd747e86975 | 1 | 6dd747e86975 | 1 |
|---|----------------|---|----------------|---|When you have a Proxmark listen in on the toy-base communication, you learn that Disney Infinity NFC toys use one key for the entire toy, both key A and key B for all five sectors is the same. Neither one can be read, so you need to know it in advance. Sector zero is read-only, and sectors 1 through 4 are readable and writable by both key A and key B.
Four sectors, three blocks each, means every toy has 192 bytes of storage we can use for our own purposes.
The other nice thing about having a Proxmark is it can simulate a MIFARE tag. I don't need to buy a bunch of Disney Infinity toys to get a bunch of keys to see if there are patterns.
I can have the Proxmark pretend to be a tag with a randomly generated ID, and then have it listen in on what key the base would use for it.
hf mf dbg 1
#db# Debug level: 1
hf 14a sim u 040FEB2A1731C0 t 6 x
Emulating ISO/IEC 14443 type A tag with 7 byte UID (040feb2a1731c0)
Press pm3-button to abort simulation
Found Key: [eff5292c270a]And when you do this, for dozens of keys in regular patterns, you find there's no pattern at all.
| UID | Key A |
|---|---|
10000000000000 |
1b052a1d4049 |
01000000000000 |
6bbea46ca610 |
00100000000000 |
5d9efcc36311 |
00010000000000 |
f8c01b9f689e |
00001000000000 |
8719aed2f84e |
00000100000000 |
75df108dc453 |
00000010000000 |
80533b9e6cae |
00000001000000 |
8c0a0b58c31e |
00000000100000 |
f8234f0d198b |
00000000010000 |
75251a0505ef |
00000000001000 |
c8388207688c |
00000000000100 |
001c576553dd |
00000000000010 |
34d3557178fe |
00000000000001 |
192ffe184056 |
When there aren't any patterns, the only solution left is to reverse-engineer the algorithm by figuring out where it lives, and then extracting it from the software or firmware, and as a liberal arts major, I don't really have the engineering experience for that.
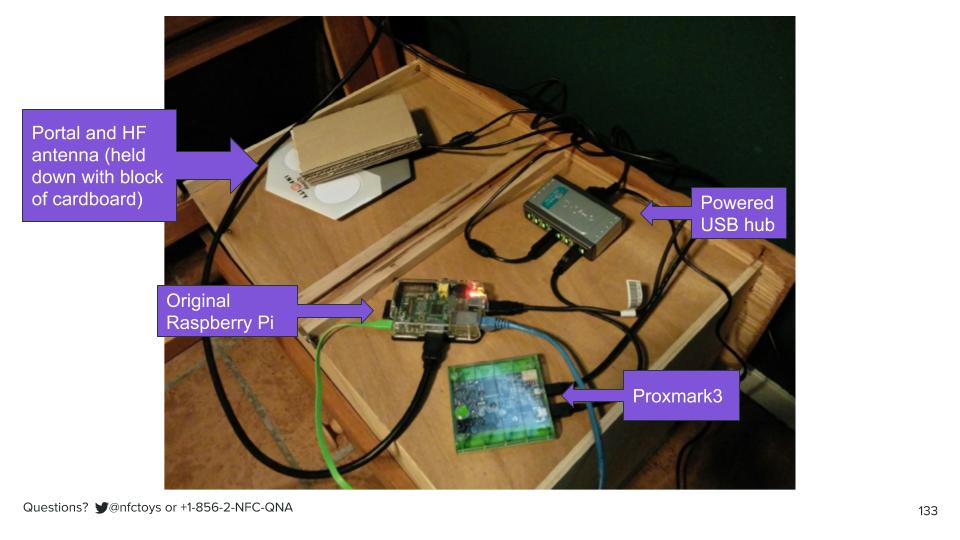
What I could do, though, is what I was just doing, but at web scale. So for about sixteen months, I ran a web service that accepted a Disney Infinity toy UID, passed it along to the Proxmark for simulation, listened in for the key, and then posted it publicly,
along with all other UIDs that had ever been requested, a kind of public UID/key database.
New interoperability for Infinity
Finally, another security researcher did have the engineering experience, and so today I can present the first, public, clean room description of an algorithm to generate the keys A and B for all Disney Infinity figures released. This algorithm supports new interoperability of Disney Infinity NFC toys.
Let a prefix be the 16-byte (32-character) hexadecimal representation of the integer computed by the multiplication of the four prime numbers 3 and 5 and 23 and 38,844,225,342,798,321,268,237,511,320,137,937
Let a postfix be the 15-byte (30-character) hexadecimal representation of the integer computed by the multiplication of the three prime numbers 3 and 7 and 9,985,861,487,287,759,675,192,201,655,940,647
Compute the SHA-1 digest of the 38 bytes encoded by the 76-character hexadecimal concatenation of the prefix and the UID and the postfix
The key A for all sectors is 6 bytes, represented in hexadecimal as 12 characters: in order, the 4th and 3rd and 2nd and 1st and 8th and 7th bytes of the computed SHA-1 digest
By knowing an algorithm used to set the read/write passwords (keys A and B), we can interoperably read/write our own data to an Infinity NFC toy, using our own NFC hardware and software, without tedious manual simulation and sniffing on a per-toy basis.
On nfc.toys, you'll find a video showing me writing custom data using a Mac with an off-the-shelf, USB NFC reader, and reading that custom data back out with an Android phone, using a standard app from the Google Play store, NXP TagInfo.
You'll also find a sample implementation of this algorithm in Python 2.
Nintendo Amiibo

There haven't been any new Skylanders figures in a year, and Disney Infinity was canceled in 2016.
But Amiibo, which is Nintendo's line of collectible figures,

playing cards, and cereal, is still going strong.
Same question as before, who has kids who demand regular new Amiibo figures?
Who personally collects Amiibo figures?
Who has been forced to pirate Amiibo figures, either buying pre-cloned tags, or cloning tags themselves, because the Amiibos you want always sell out before you can get one?
For everyone else, Nintendo launched Amiibo in 2014, and in classic Nintendo fashion, treats them as much as rare collectables for obsessive adults as video game accessories for kids, resulting in lines in front of stores on release days, and toys selling out and never being reissued.

Because NFC support is built into Nintendo's Wii U, New 3DS, and Switch consoles, no game-specific reader is necessary for any game to provide Amiibo support, you just swipe the toy right across the controller. What each Amiibo toy does in each game varies by game: some only support specific figures, some store gameplay data on the figure, some will recognize any figure. Nintendo lists over sixty games in the US with Amiibo support, and over 160 toys. (There are additional Japan-exclusive figures and games.)

This is a "Duck Hunt" figure from Nintendo Amiibo as seen in NXP TagInfo.
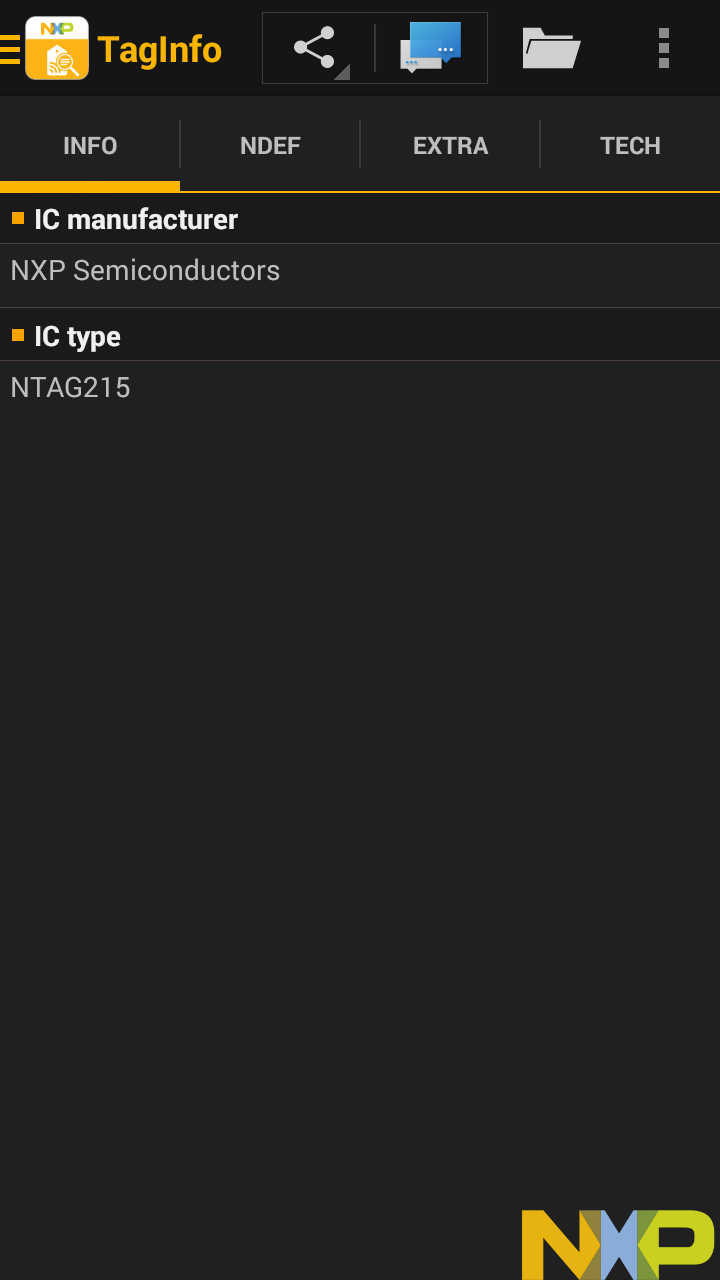

NXP TagInfo says Duck Hunt is also an NXP, this one a Type 2 tag called NTAG215,
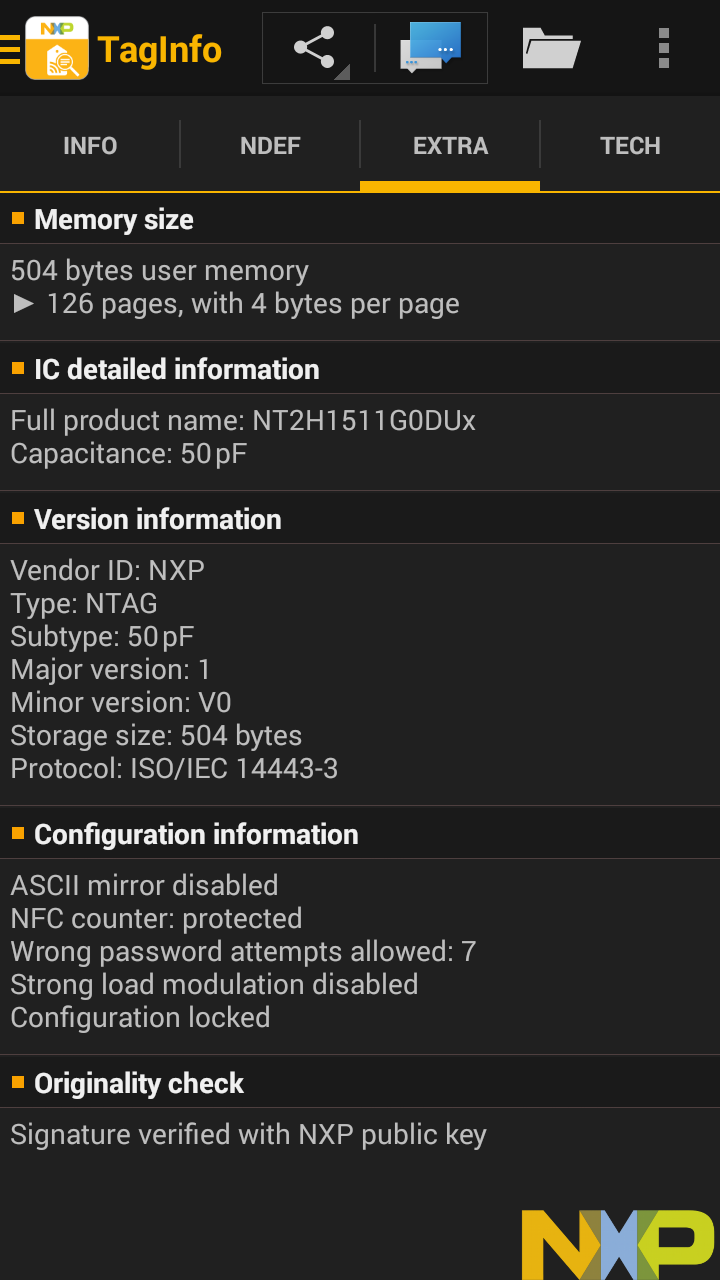
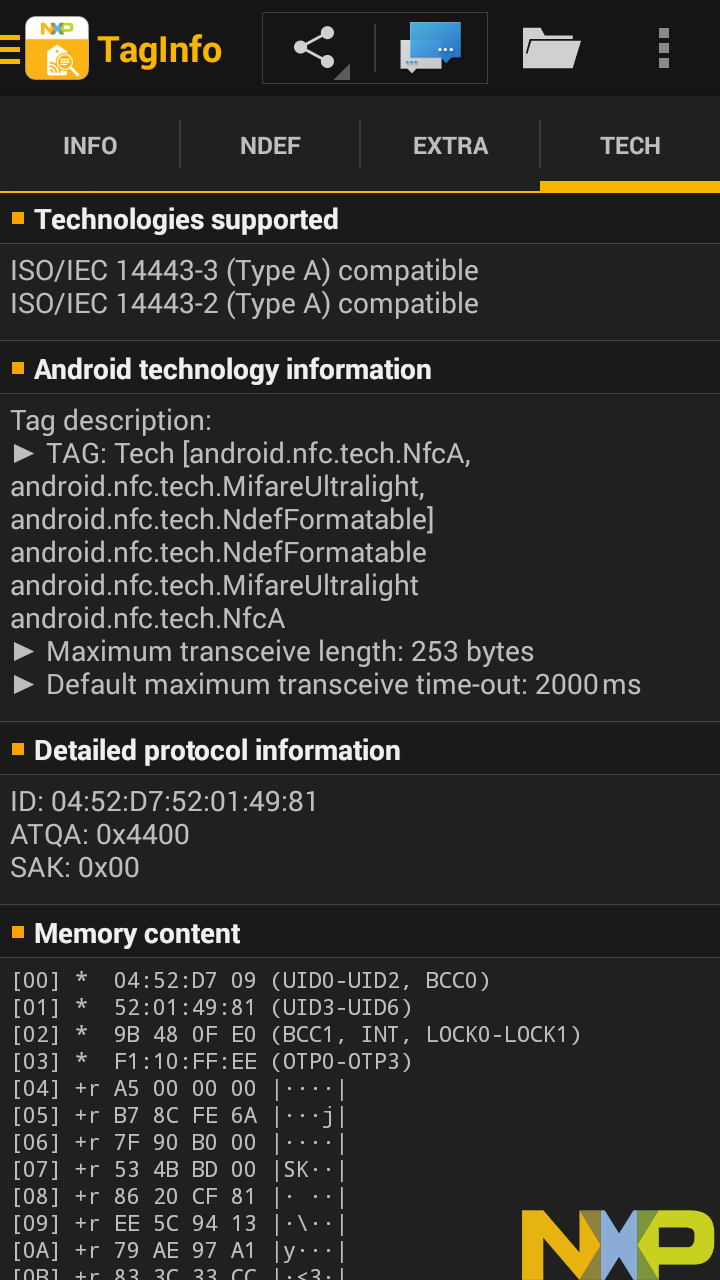
with 504 bytes, made up of 126 "pages" with 4 bytes per page, similar to that pair of Bluetooth headphones.
Here's the memory content.
[00] * 04:52:D7 09 (UID0-UID2, BCC0)
[01] * 52:01:49:81 (UID3-UID6)
[02] * 9B 48 0F E0 (BCC1, INT, LOCK0-LOCK1)
[03] * F1:10:FF:EE (OTP0-OTP3)
[04] +r A5 00 00 00 |....|
[05] +r B7 8C FE 6A |...j|
[06] +r 7F 90 B0 00 |....|
[07] +r 53 4B BD 00 |SK..|
[08] +r 86 20 CF 81 |. ..|
[09] +r EE 5C 94 13 |.\..|
[0A] +r 79 AE 97 A1 |y...|
[0B] +r 83 3C 33 CC |.<3.|
[0C] +r C2 E8 B5 B9 |....|
[0D] *r 2F 4A 39 0A |/J9.|
[0E] *r A8 FA 02 12 |....|
[0F] *r 57 55 BD 07 |WU..|
[10] *r BD B6 C0 E3 |....|
[11] *r 9D 5B EA 74 |.[.t|
[12] *r DC EC 08 5E |...^|
[13] *r 0D 6F 7B 2E |.o{.|
[14] *r A7 0A 62 5C |..b\|
[15] *r 07 82 00 00 |....|
[16] *r 00 2F 00 02 |./..|
[17] *r 0D 12 75 01 |..u.|
[18] *r CA 37 02 A9 |.7..|
[19] *r 39 47 7C F0 |9G|.|
[1A] *r DA 03 67 C8 |..g.|
[1B] *r B3 8B F1 A2 |....|
[1C] *r 6B 52 9E 73 |kR.s|
[1D] *r 7F FA 80 A7 |....|
[1E] *r AC 4D 9D 83 |.M..|
[1F] *r FB 9D 9F 1C |....|
[20] +r 6E 97 C0 48 |n..H|
[21] +r 2E 84 0D 09 |....|
[22] +r E4 6E B3 15 |.n..|
[23] +r B6 31 4F BA |.1O.|
[24] +r E1 31 28 39 |.1(9|
[25] +r 7F 7C F5 85 |.|..|
[26] +r 2E 5C AD 49 |.\.I|
[27] +r 9E 86 CA EE |....|
[28] +r D0 4D A1 84 |.M..|
[29] +r 67 DA EB 44 |g..D|
[2A] +r EE 0D 10 EA |....|
[2B] +r D1 76 54 C6 |.vT.|
[2C] +r 53 F1 B0 55 |S..U|
[2D] +r D9 96 00 38 |...8|
[2E] +r 4E C3 92 BD |N...|
[2F] +r 14 7D 55 D6 |.}U.|
[30] +r A5 3C 18 52 |.<.R|
[31] +r 02 F8 80 92 |....|
[32] +r FF B9 4C 77 |..Lw|
[33] +r C3 18 8F 23 |...#|
[34] +r 15 62 EB 24 |.b.$|
[35] +r E6 C1 33 BA |..3.|
[36] +r 2D 70 97 34 |-p.4|
[37] +r 8F 8C 10 1E |....|
[38] +r D2 DE 1A E4 |....|
[39] +r 3A F2 D6 5C |:..\|
[3A] +r E1 4E 47 87 |.NG.|
[3B] +r 7F 4A 29 B0 |.J).|
[3C] +r DF F0 B4 09 |....|
[3D] +r 07 E1 8C 07 |....|
[3E] +r B2 F5 5F 2C |.._,|
[3F] +r BC 1E 40 51 |..@Q|
[40] +r 2F B8 CE 6D |/..m|
[41] +r 8A A9 2D EC |..-.|
[42] +r BE 61 0D A6 |.a..|
[43] +r 2D 80 31 F2 |-.1.|
[44] +r 6E 62 39 A7 |nb9.|
[45] +r 71 35 5B A6 |q5[.|
[46] +r 84 BA DF 4B |...K|
[47] +r 2E DC BC 2C |...,|
[48] +r 40 FA 45 B5 |@.E.|
[49] +r 11 01 51 57 |..QW|
[4A] +r 92 D1 B9 AB |....|
[4B] +r 0F E3 4E 9E |..N.|
[4C] +r C3 4A 6E 54 |.JnT|
[4D] +r 32 F0 CA 7C |2..||
[4E] +r AE 02 80 07 |....|
[4F] +r 82 38 89 C3 |.8..|
[50] +r 5B CB F1 21 |[..!|
[51] +r EE 3B 3B E5 |.;;.|
[52] +r 04 DF 18 B2 |....|
[53] +r 02 0A F3 B1 |....|
[54] +r 4F 0C 3B CF |O.;.|
[55] +r B3 43 68 B8 |.Ch.|
[56] +r DD 62 3A 61 |.b:a|
[57] +r 9C 46 89 81 |.F..|
[58] +r 0B C7 44 2C |..D,|
[59] +r 49 53 34 B6 |IS4.|
[5A] +r C3 40 9A 1B |.@..|
[5B] +r A0 8F A6 56 |...V|
[5C] +r CE 58 07 11 |.X..|
[5D] +r BE DA 87 00 |....|
[5E] +r 4F F6 45 FA |O.E.|
[5F] +r B7 55 90 E7 |.U..|
[60] +r 10 0F 77 A1 |..w.|
[61] +r FF DC 28 C9 |..(.|
[62] +r B7 A0 9F 7A |...z|
[63] +r FF 66 22 05 |.f".|
[64] +r 4E 5D A6 15 |N]..|
[65] +r B7 88 63 BF |..c.|
[66] +r 76 39 BF E0 |v9..|
[67] +r 64 B0 FA B7 |d...|
[68] +r 3A 05 BF 2F |:../|
[69] +r 7E 7B 04 2F |~{./|
[6A] +r C1 C1 40 D7 |..@.|
[6B] +r 63 C0 F6 71 |c..q|
[6C] +r 41 12 11 51 |A..Q|
[6D] +r 34 F5 24 F5 |4.$.|
[6E] +r 2B CF 2C B1 |+.,.|
[6F] +r 20 2E 73 9F | .s.|
[70] +r 9E 07 E9 7E |...~|
[71] +r 2A C3 A2 6D |*..m|
[72] +r 8E A7 46 99 |..F.|
[73] +r EB E3 17 60 |...`|
[74] +r AC DC 67 41 |..gA|
[75] +r D8 1A 6E 46 |..nF|
[76] +r 03 81 43 E0 |..C.|
[77] +r DE C0 EE 31 |...1|
[78] +r 8E 13 BF 8C |....|
[79] +r 16 B7 7B FB |..{.|
[7A] +r BC B3 D4 FA |....|
[7B] +r 17 F0 CE 4A |...J|
[7C] +r FF 56 4C 3F |.VL?|
[7D] +r 25 24 8A 24 |%$.$|
[7E] +r E3 D4 DE DA |....|
[7F] +r 30 50 5C F3 |0P\.|
[80] +r 5B F2 6D 7E |[.m~|
[81] +r 3E C7 B9 BF |>...|
[82] *r 01 00 0F BD (LOCK2-LOCK4, CHK)
[83] *r 00 00 00 04 (CFG, MIRROR, AUTH0)
[84] *r 5F 00 -- -- (ACCESS)
[85] +P XX XX XX XX (PWD0-PWD3)
[86] +P XX XX -- -- (PACK0-PACK1)
*:locked & blocked, x:locked,
+:blocked, .:un(b)locked, ?:unknown
r:readable (write-protected),
p:password protected, -:write-only
P:password protected write-only
Unlike the Disney Infinity figure, nearly all of the Amiibo is readable, but some of it is marked as "locked & blocked" or "blocked."
If we were figuring out Amiibo ourselves, we'd have to work it like we did Disney Infinity, but we're luckier here in two ways.
First, by the time I got around to trying Amiibo toys, researcher Marcos Del Sol Vives had already figured out how to derive their password from the toy's UID,
and services for it
and code have been published across the internet since.
Second, many of us could probably have independently replicated his work, just like fellow HOPE 2018 speaker James Chambers did.
While the Skylanders math was pretty gnarly, the Amiibo math, as presented, is a bitwise exclusive OR operation.
It's simple enough that you can do it by hand, with pen and paper, enabling us to write 428 bytes of our own data onto any Amiibo NFC toy.
New interoperability for Amiibo

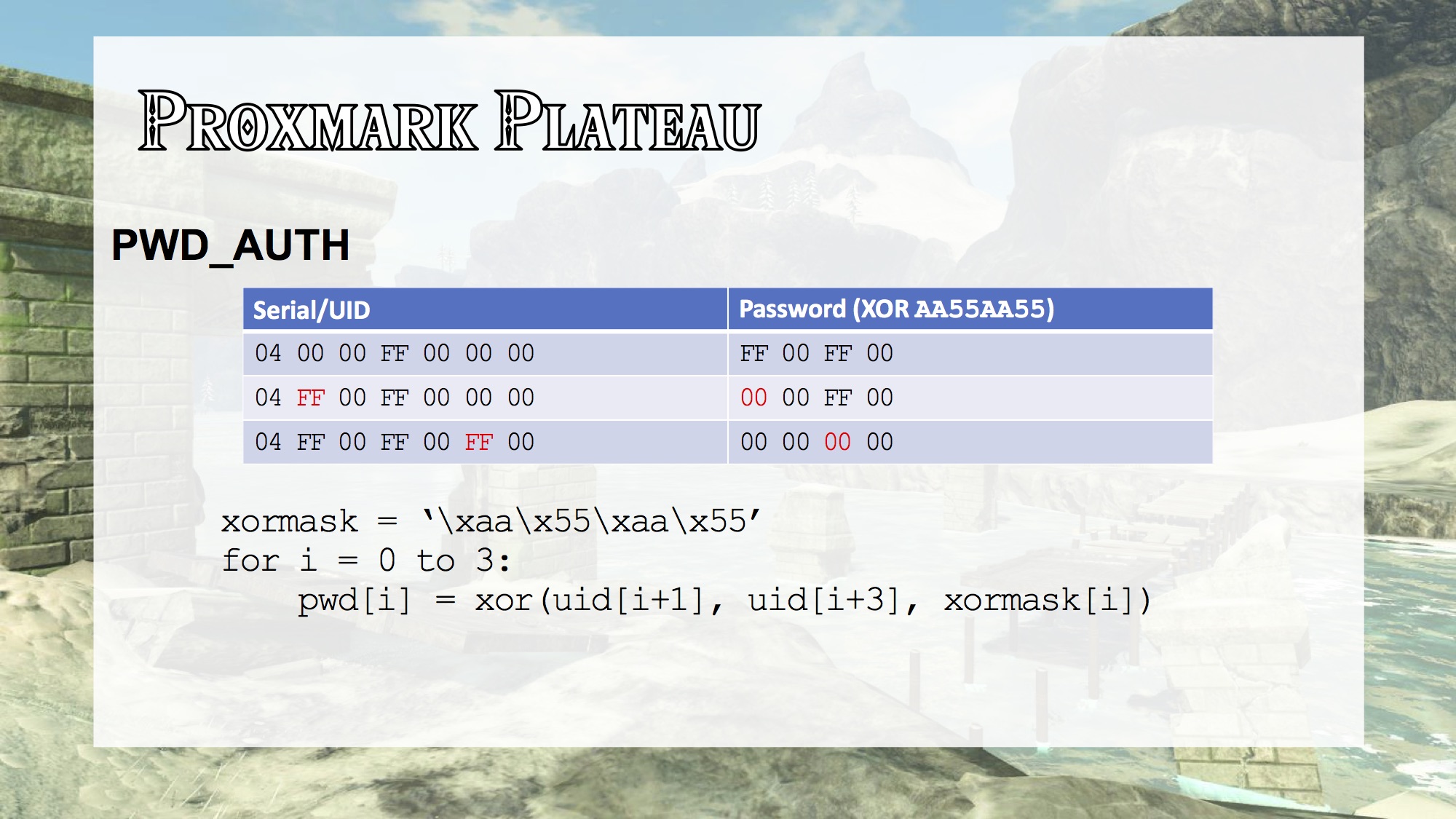
So, today, along with presenting a public, clean room description of an algorithm to generate the PWD for current Amiibo figures, I'm also handing out a worksheet, with an Amiibo card and its UID, so you can generate the PWD by hand yourself, right now, in your seat, if you'd like. These support new interoperability of Nintendo Amiibo NFC toys.
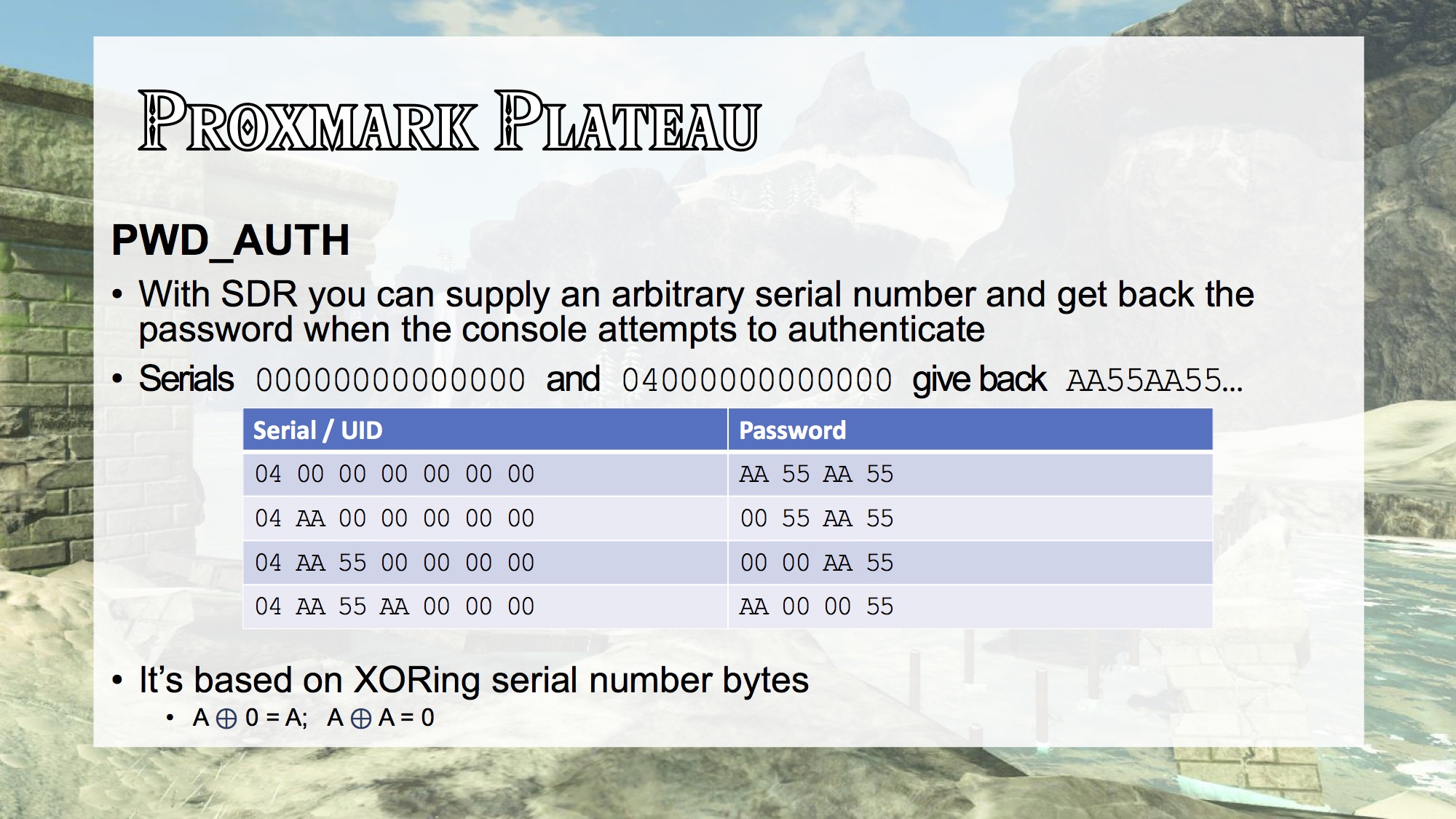
The Amiibo UID is seven digits in hexadecimal, e.g.
04:52:D7:52:01:49:81. We'll refer to them asUID 0throughUID 6. The resulting PWD is four digits in hexadecimal, e.g.aa:83:b1:d5. We'll refer to them asPWD 0throughPWD 3.
UID 1xorUID 3xoraa=PWD 0UID 2xorUID 4xor55=PWD 1UID 3xorUID 5xoraa=PWD 2UID 4xorUID 6xor55=PWD 3
By knowing an algorithm used to set the write password (PWD), we can interoperably write our own data to an Amiibo NFC toy, using our own NFC hardware and software, without needing to compute the PWD by hand on a per-toy basis.
On nfc.toys, you'll find a video showing me writing custom data using a Raspberry Pi using an off-the-shelf, NFC add-on, and reading that custom data back out with a Windows 10 laptop, using the open source Google Chrome App NFC Library.
You'll also find a sample implementation of this algorithm in Python 2.

Before I hand out the worksheets, though, it's important to consider those legal subtleties I mentioned. Can we get in some sort of trouble if we do this?
DMCA
A few points of order again.
First, I'm about to talk about legal stuff, but I am not an attorney, and this is not legal advice.
If you intend to publicly discuss or publish your own NFC toy efforts, especially if you explore areas beyond what this talk covers, like data encryption or the USB reader hardware, and you're a US citizen or ever intend to visit the US afterwards, you should talk with an attorney first. Your local bar association can usually refer you to an appropriate attorney, often with a free or reduced-cost initial conversation.
(If you are interested in exploring the USB reader hardware, the end of the DMCA concerns documentation has some analysis and references which may be useful.)

Second, this is America, where you can be sued by anyone at any time for any reason, and then you're stuck having to defend yourself. This is lawsuit as threat model. If you can't afford to defend yourself, you should be taking that into consideration.
Third, while the next several minutes may be an interesting discussion, at the end of the day, our opinion doesn't matter. Everything we're going to cover is a grey area, and I'll be positioning it as such, because it's things that can only be decided by a judge in a court.

Alright, so why are we suddenly talking about legal trouble, when I've just discussed a long history of security research and academic scholarship,
Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards
Comprehensive security analyses of a toys-to-life game and possible countermeasures
some even acknowledged by the companies affected, which actively and directly discuss security compromises in these NFC tags, and am just taking the next steps?
The reason is that, legally, some NFC toys may not count as regular NFC tags. Let's define NFC toys in a way that might help clarify this.
The interaction is typically digital, and is important.
There are probably toys that embed NFC tags for tracking or anti-counterfeiting purposes, and we just don't know about them. Toys that use NFC to support interactions, typically digital ones, means the toy may contain, affect, or involve digital content, which may be covered by copyright.
In 1998, the United States passed the Digital Millennium Copyright Act, or DMCA. Most of you probably know it for section 512, which establishes the "safe harbor" provisions for online hosts. This is when a copyright owner notifies your upstream provider, like your ISP or web host, that you've put their copyrighted content online, and the upstream provider needs to take it down.
That's not the part we're concerned with. There's a different part of the DMCA, section 1201, known as the "anti-circumvention" provisions. 1201 establishes that circumventing, or working around, any type of copy-protection mechanism, is a crime, as is distributing tools to support others' circumventions. You can be sued by the copyright owner whose digital locks you picked, a civil action, and also be charged by the federal government, a criminal action. If it's a criminal action, this is the damage:
For the first criminal violation of Title I of the DMCA (§§ 1201, 1202), the maximum penalty is five years’ imprisonment, a $500,000 fine or twice the monetary gain or loss, or both imprisonment and a fine. 17 U.S.C. §§ 1204, 3571(d). For subsequent offenses, the maximum penalty is ten years’ imprisonment, a $1 million fine or twice the monetary gain or loss, or both imprisonment and a fine.
It doesn't matter whether you can or do use an NFC toy with the video game it was intended for. That it may be intended to protect copyrighted content is what makes any possible circumvention illegal.
Anti-circumvention
So, maybe, let's take this seriously, and see how the DMCA concerns us, based on excerpts from the 2013 Department of Justice Prosecuting Intellectual Property Crimes manual, fourth edition.
To prove a violation of 17 U.S.C. §§ 1201(a)(1) and 1204, the government must establish that the defendant
- willfully
- circumvented
- a technological measure that effectively controls access (i.e., an access control)
- to a copyrighted work
- for commercial advantage or private financial gain.
Let's take those one at a time:
"willfully"
The majority rule in criminal copyright cases for a higher standard of willfulness is also generally consistent with civil copyright cases. The issue arises in civil cases when plaintiffs attempt to recover increased statutory damages, which are available only for willful infringement. 17 U.S.C. § 504(c). Whereas criminal willfulness requires a specific intent to violate “a known legal duty,” civil cases require a more specific intent to violate copyright laws; that is that willfulness is not just an intent to copy, but rather an intent to infringe.
"Willfully" has a specific legal meaning, but let's just go with the idea that since you're all in this room, you can't argue that you didn't know it might not be okay for you to do this. Someone who just comes across those clean room algorithms might have a stronger case.
"circumvented"
In other words, circumvention of an access control occurs when someone bypasses the technological measure’s gatekeeping capacity, thereby precluding the copyright owner from determining which users have permission to access the digital copyrighted work and which do not.
Arguably, “a person circumvents a technological measure only when he affirmatively performs an action that disables or voids the measure that was installed to prevent them from accessing the copyrighted material.”
Circumvention does not occur, however, by properly using the technological measure’s gatekeeping capacity without the copyright owner’s permission.
Even if buying the toy legally doesn't grant us the right to crack its keys and put our own data on it, once we have the keys, we're not bypassing anything. We're using the keys as intended. (Now, we might be eligible for other charges under other laws, but not a DMCA violation.)
"a technological measure that effectively controls access"
An access control “effectively controls access to a work” if its ordinary function and operation is to control access to a copyrighted work’s expression, regardless of whether or not the control is a strong means of protection.
Significantly, courts have rejected the argument that the meaning of the term “effectively” is based on how successful the technological measure is in controlling access to a copyrighted work.
Obviously, an NFC tag's keys or passwords are "technological measures." "Effectively" is a great example of legalese not being plain English, despite sounding like it. "Effectively" does not mean what it does to us in this room, where you're probably interpreting it as something along the lines of "does a good job at." In court, "effectively" basically means "does it exist to do this."
"to a copyrighted work"
The protection of a copyrighted work is an essential element.
The DMCA’s anti-circumvention prohibition does not apply to someone who circumvents access controls to a work in the public domain, like a book of Shakespeare, because such a protection measure controls access to a work that is not copyrighted.
If we're just just talking about the toy right now, and the existing data on the toy, then if that data is just facts and figures, it wouldn't be copyrighted, and therefore breaking into the NFC toy wouldn't be an infringement.
"for commercial advantage or private financial gain."
Essentially, a defendant has acted for “commercial advantage or private financial gain” if he sought a profit, financial or otherwise.
“Financial gain” is broadly defined to include not only a monetary transaction, but also the “receipt, or expectation of receipt, of anything of value, including the receipt of other copyrighted works.”
Whether a defendant actually makes a profit is beside the point: what matters is that he intended to profit.
These courts held that the mere purchase and use of such a device [unauthorized satellite and cable television decoders] for the defendant’s own benefit and that of his family and friends does not constitute “gain” within the meaning of that statute.
If you're just using these toys yourself, for yourself, there's no commercial advantage or private financial gain. If you're selling keys? Maybe that's an issue? But I'm not being paid to give this talk, and the content on nfc.toys is deeded to the public domain, so I hope that's evidence enough of my lack of profit motive.
So here's where we stand:
| Requirement | Our best guess |
|---|---|
| 1. willfully | Maybe? |
| 2. circumvented | Maybe not? |
| 3. a technological measure that effectively controls access (i.e., an access control) | Maybe? |
| 4. to a copyrighted work | Maybe not? |
| 5. for commercial advantage or private financial gain. | Maybe not? |
(A civil action doesn't need to address #1 or #5.)
If we're only talking about the toy right now, and only about the existing data on the toy, because we need to tick all the boxes, if the data on the NFC toy is not a copyrighted work, then maybe we're not violating the DMCA, either civilly or criminally!
That doesn't mean we can't be sued for this anyway! It just means if we can afford to defend ourselves, we might have a defensible case.
Evaluating toy data
If part of our legal standing depends on the data on the toy not being copyrightable, how can we figure that out? Let's start by looking at what copyright protects.
A work must be an original, creative expression of an idea or concept, and it must be recorded in tangible form. Thus, copyright law protects a novel or poem written on paper or typed in a computer, a song recorded in a studio or written on sheet music, a sculpture modeled in clay or bronze, or a computer program on a computer’s hard disk.
If the data includes things like, the actual character art and sound effects which get used in the game? Those would be original creative expressions.
If the data is just "This is a Ninjini toy, with this health and this experience level," those are discrete facts and figures. They're not creative expressions. Facts and figures alone are not copyrightable.
So, how can we tell if the data is uncopyrightable facts and figures, or copyrightable content?
There's a few ways. Some researchers might reverse-engineer the video game or its support code to understand what data gets read or written. Others might reverse-engineer the encryption on the data, reading it from the tag frequently to see what changes get made.
But this is a talk focusing just on the NFC tag in an NFC toy, and it turns out there's a lot we can learn without doing any additional work at all. All we need to do is very carefully play the game, and pay close attention to the tag.
I go into more detail on nfc.toys, but the short version is, we can absolutely collect evidence that there isn't anything original or copyrightable on a figure.
Being careful about changing things in game means we can figure out which blocks are likely to store many of our character's variables.
These are blocks that Skylanders: Giants writes to the Ninjini toy during gameplay:
00000000000000000000000000000000
00000000000000000000000000000000
00000000000000000000000000000000
edb9a575cc357f0f0869000000000000
5b00e0d3a691ea9d6a93c93348c35d5f
b893ce40958a66d3faee5c5a8cb15116
3982b1519ae73c4c2e83f19c8545c2c8
cbd471261bf67f0f0869000000000000
0f5dc22225ac4cc829f13c9bb5b945a6
70574d5c8be3164624e04abb9225c0aa
b4fb860161020cd3a69ef8ec2b49db23
58e29b8ff0177f0f0869000000000000
78330690ea993234f430bd9ffbbe4ca2
43968ac84bb0b4099a25a49732a5f831
4d0ab7ac143273852a7797097d402024
143833285e907f0f0869000000000000
2f0b587954b1d9359c3e839e24084a8d
3e9b2242b05332dccd47743fb94ff797
00000000000000000000000000000000
870ed981b5717f0f0869000000000000
By watching the clock, we can see that these two blocks probably store some sort of playtime counter:
(00:00 playtime, 00:31 playtime, 00:34 playtime)
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000
5b00e0d3a691ea9d6a93c93348c35d5f 78c7c394aa2eda7867af9cd63906659f efe969b9c7d277b7fbde4598e65f2b63
b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116
3982b1519ae73c4c2e83f19c8545c2c8 3982b1519ae73c4c2e83f19c8545c2c8 3982b1519ae73c4c2e83f19c8545c2c8
cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000
0f5dc22225ac4cc829f13c9bb5b945a6 0f5dc22225ac4cc829f13c9bb5b945a6 0f5dc22225ac4cc829f13c9bb5b945a6
70574d5c8be3164624e04abb9225c0aa 4914b24c7903b2ef9133882b11d2f51e c57971fb41d5ebc340dc92cc072640ff
b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23
58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000
78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2
43968ac84bb0b4099a25a49732a5f831 43968ac84bb0b4099a25a49732a5f831 43968ac84bb0b4099a25a49732a5f831
4d0ab7ac143273852a7797097d402024 4d0ab7ac143273852a7797097d402024 4d0ab7ac143273852a7797097d402024
143833285e907f0f0869000000000000 143833285e907f0f0869000000000000 143833285e907f0f0869000000000000
2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d
3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000
By testing different nicknames, we can see that these two blocks store the nickname, and that they change depending on its length:
("Ninjini" (default), "Securitoy", "bob")
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000
efe969b9c7d277b7fbde4598e65f2b63 33221aade2316dfd5c68b62a46c7e911 1d732b75d33aff25f2675c9b44ef1fbb
b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116
3982b1519ae73c4c2e83f19c8545c2c8 b6b1cc7a0cb42f27ea5904cfefa9d17b be08da56d4294d3a3cea3d462bbab45e
cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000
0f5dc22225ac4cc829f13c9bb5b945a6 dad957d41b2b6bb12b34c32a77f92335 0f5dc22225ac4cc829f13c9bb5b945a6
70574d5c8be3164624e04abb9225c0aa aa649ef00de18bf1c89792937927929e b77b34ce26cb9bd4e6fef26750d59a5b
b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23
58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000
78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2
43968ac84bb0b4099a25a49732a5f831 43968ac84bb0b4099a25a49732a5f831 43968ac84bb0b4099a25a49732a5f831
4d0ab7ac143273852a7797097d402024 4d0ab7ac143273852a7797097d402024 4d0ab7ac143273852a7797097d402024
143833285e907f0f0869000000000000 143833285e907f0f0869000000000000 143833285e907f0f0869000000000000
2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d
3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000
By gaining gold and experience, we can see that the same blocks that store the playtime counters probably also store gold, and that these new blocks seem to store experience:
(10 gold, 383 gold, 403 gold)
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000 edb9a575cc357f0f0869000000000000
c10c9917b7cca1505bcb88c40479fe90 5e6f94dd891779642da4faa97f7d275a e8c53fe93a94832139f37d03038b3edb
b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116 b893ce40958a66d3faee5c5a8cb15116
3982b1519ae73c4c2e83f19c8545c2c8 3982b1519ae73c4c2e83f19c8545c2c8 3982b1519ae73c4c2e83f19c8545c2c8
cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000 cbd471261bf67f0f0869000000000000
0f5dc22225ac4cc829f13c9bb5b945a6 0f5dc22225ac4cc829f13c9bb5b945a6 0f5dc22225ac4cc829f13c9bb5b945a6
419335db4cf15ec339c62403c0921f87 006490a30d7a5756424a3e17ca04603f 3a6f8b5efc773d7747709a4fd68ffa44
b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23 b4fb860161020cd3a69ef8ec2b49db23
58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000 58e29b8ff0177f0f0869000000000000
78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2 78330690ea993234f430bd9ffbbe4ca2
43968ac84bb0b4099a25a49732a5f831 2d93b86788d89d9595e416adce75238e 2d93b86788d89d9595e416adce75238e
4d0ab7ac143273852a7797097d402024 9601bfb99c07e369a272ff8295d5677a 9601bfb99c07e369a272ff8295d5677a
143833285e907f0f0869000000000000 143833285e907f0f0869000000000000 143833285e907f0f0869000000000000
2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d 2f0b587954b1d9359c3e839e24084a8d
3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797 3e9b2242b05332dccd47743fb94ff797
00000000000000000000000000000000 00000000000000000000000000000000 00000000000000000000000000000000
870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000 870ed981b5717f0f0869000000000000
The NFC tags in these NFC toys are merely storage devices for numeric and text data that track your character's progress, which can't be covered by copyright.
Anti-circumvention revisited
There's one other concern, we touched on it briefly before. Even if we're not circumventing an access control to read and write toy data, the toys are still used to access content within a game, and the game content is almost certainly under copyright.
That list again:
| Requirement | Our best guess | |
|---|---|---|
| for data on the toy | for video game content | |
| 1. willfully | Maybe? | Maybe? |
| 2. circumvented | Maybe not? | Maybe not? |
| 3. a technological measure that effectively controls access (i.e., an access control) | Maybe? | ??? |
| 4. to a copyrighted work | Maybe not? | Maybe? |
| 5. for commercial advantage or private financial gain. | Maybe not? | Maybe not? |
If we're changing #4 to mean "the game content" instead of "the data on the toy," how does that change #3? Are the NFC tag keys and passwords effective access controls that protect the game content?
I think the additional argument here hinges on that particular legal definition of the term, effectively. That is, the point of the NFC tag keys and passwords isn't to protect the game content, they're there only to protect the data on the tag.
Every NFC toy that controls access to content in a video game requires at least its initial presence on an NFC reader to access that content, suggesting the access control for the game content is the NFC toy as a physical object, in combination with the reader, plus the code in the game, all together.
Every NFC toy we've looked at uses keys and passwords in different ways, but they are all able to perform that same function in that same combination, despite those differences.
The Valk thesis asserts that:
Using a static key for sector zero shows a misunderstanding of the NFC technology.
[00] * 04:52:D7 09 (UID0-UID2, BCC0)
[01] * 52:01:49:81 (UID3-UID6)
[02] * 9B 48 0F E0 (BCC1, INT, LOCK0-LOCK1)
[03] * F1:10:FF:EE (OTP0-OTP3)
[04] +r A5 00 00 00 |....|
[05] +r B7 8C FE 6A |...j|
[06] +r 7F 90 B0 00 |....|
[07] +r 53 4B BD 00 |SK..|
[08] +r 86 20 CF 81 |. ..|
[09] +r EE 5C 94 13 |.\..|
[0A] +r 79 AE 97 A1 |y...|
[0B] +r 83 3C 33 CC |.<3.|
[0C] +r C2 E8 B5 B9 |....|
[0D] *r 2F 4A 39 0A |/J9.|
[0E] *r A8 FA 02 12 |....|
[0F] *r 57 55 BD 07 |WU..|
[10] *r BD B6 C0 E3 |....|
[11] *r 9D 5B EA 74 |.[.t|
[12] *r DC EC 08 5E |...^|
[13] *r 0D 6F 7B 2E |.o{.|
[14] *r A7 0A 62 5C |..b\|
[15] *r 07 82 00 00 |....|
[16] *r 00 2F 00 02 |./..|
[17] *r 0D 12 75 01 |..u.|
[18] *r CA 37 02 A9 |.7..|
[19] *r 39 47 7C F0 |9G|.|
[1A] *r DA 03 67 C8 |..g.|
[1B] *r B3 8B F1 A2 |....|
[1C] *r 6B 52 9E 73 |kR.s|
[1D] *r 7F FA 80 A7 |....|
[1E] *r AC 4D 9D 83 |.M..|
[1F] *r FB 9D 9F 1C |....|
[20] +r 6E 97 C0 48 |n..H|
[21] +r 2E 84 0D 09 |....|
[22] +r E4 6E B3 15 |.n..|
[23] +r B6 31 4F BA |.1O.|
[24] +r E1 31 28 39 |.1(9|
[25] +r 7F 7C F5 85 |.|..|
[26] +r 2E 5C AD 49 |.\.I|
[27] +r 9E 86 CA EE |....|
[28] +r D0 4D A1 84 |.M..|
[29] +r 67 DA EB 44 |g..D|
[2A] +r EE 0D 10 EA |....|
[2B] +r D1 76 54 C6 |.vT.|
[2C] +r 53 F1 B0 55 |S..U|
[2D] +r D9 96 00 38 |...8|
[2E] +r 4E C3 92 BD |N...|
[2F] +r 14 7D 55 D6 |.}U.|
[30] +r A5 3C 18 52 |.<.R|
[31] +r 02 F8 80 92 |....|
[32] +r FF B9 4C 77 |..Lw|
[33] +r C3 18 8F 23 |...#|
[34] +r 15 62 EB 24 |.b.$|
[35] +r E6 C1 33 BA |..3.|
[36] +r 2D 70 97 34 |-p.4|
[37] +r 8F 8C 10 1E |....|
[38] +r D2 DE 1A E4 |....|
[39] +r 3A F2 D6 5C |:..\|
[3A] +r E1 4E 47 87 |.NG.|
[3B] +r 7F 4A 29 B0 |.J).|
[3C] +r DF F0 B4 09 |....|
[3D] +r 07 E1 8C 07 |....|
[3E] +r B2 F5 5F 2C |.._,|
[3F] +r BC 1E 40 51 |..@Q|
[40] +r 2F B8 CE 6D |/..m|
[41] +r 8A A9 2D EC |..-.|
[42] +r BE 61 0D A6 |.a..|
[43] +r 2D 80 31 F2 |-.1.|
[44] +r 6E 62 39 A7 |nb9.|
[45] +r 71 35 5B A6 |q5[.|
[46] +r 84 BA DF 4B |...K|
[47] +r 2E DC BC 2C |...,|
[48] +r 40 FA 45 B5 |@.E.|
[49] +r 11 01 51 57 |..QW|
[4A] +r 92 D1 B9 AB |....|
[4B] +r 0F E3 4E 9E |..N.|
[4C] +r C3 4A 6E 54 |.JnT|
[4D] +r 32 F0 CA 7C |2..||
[4E] +r AE 02 80 07 |....|
[4F] +r 82 38 89 C3 |.8..|
[50] +r 5B CB F1 21 |[..!|
[51] +r EE 3B 3B E5 |.;;.|
[52] +r 04 DF 18 B2 |....|
[53] +r 02 0A F3 B1 |....|
[54] +r 4F 0C 3B CF |O.;.|
[55] +r B3 43 68 B8 |.Ch.|
[56] +r DD 62 3A 61 |.b:a|
[57] +r 9C 46 89 81 |.F..|
[58] +r 0B C7 44 2C |..D,|
[59] +r 49 53 34 B6 |IS4.|
[5A] +r C3 40 9A 1B |.@..|
[5B] +r A0 8F A6 56 |...V|
[5C] +r CE 58 07 11 |.X..|
[5D] +r BE DA 87 00 |....|
[5E] +r 4F F6 45 FA |O.E.|
[5F] +r B7 55 90 E7 |.U..|
[60] +r 10 0F 77 A1 |..w.|
[61] +r FF DC 28 C9 |..(.|
[62] +r B7 A0 9F 7A |...z|
[63] +r FF 66 22 05 |.f".|
[64] +r 4E 5D A6 15 |N]..|
[65] +r B7 88 63 BF |..c.|
[66] +r 76 39 BF E0 |v9..|
[67] +r 64 B0 FA B7 |d...|
[68] +r 3A 05 BF 2F |:../|
[69] +r 7E 7B 04 2F |~{./|
[6A] +r C1 C1 40 D7 |..@.|
[6B] +r 63 C0 F6 71 |c..q|
[6C] +r 41 12 11 51 |A..Q|
[6D] +r 34 F5 24 F5 |4.$.|
[6E] +r 2B CF 2C B1 |+.,.|
[6F] +r 20 2E 73 9F | .s.|
[70] +r 9E 07 E9 7E |...~|
[71] +r 2A C3 A2 6D |*..m|
[72] +r 8E A7 46 99 |..F.|
[73] +r EB E3 17 60 |...`|
[74] +r AC DC 67 41 |..gA|
[75] +r D8 1A 6E 46 |..nF|
[76] +r 03 81 43 E0 |..C.|
[77] +r DE C0 EE 31 |...1|
[78] +r 8E 13 BF 8C |....|
[79] +r 16 B7 7B FB |..{.|
[7A] +r BC B3 D4 FA |....|
[7B] +r 17 F0 CE 4A |...J|
[7C] +r FF 56 4C 3F |.VL?|
[7D] +r 25 24 8A 24 |%$.$|
[7E] +r E3 D4 DE DA |....|
[7F] +r 30 50 5C F3 |0P\.|
[80] +r 5B F2 6D 7E |[.m~|
[81] +r 3E C7 B9 BF |>...|
[82] *r 01 00 0F BD (LOCK2-LOCK4, CHK)
[83] *r 00 00 00 04 (CFG, MIRROR, AUTH0)
[84] *r 5F 00 -- -- (ACCESS)
[85] +P XX XX XX XX (PWD0-PWD3)
[86] +P XX XX -- -- (PACK0-PACK1)
*:locked & blocked, x:locked,
+:blocked, .:un(b)locked, ?:unknown
r:readable (write-protected),
p:password protected, -:write-only
P:password protected write-only
Amiibos don't have read protection.

Another toy we didn't even get to discuss, the Pokemon Rumble U figures, don't even have write protection, you can do whatever you want with them right out of the pokeball.
This suggests that the NFC tag keys and passwords aren't "effective access controls" for the game content; they don't exist to have any affect on access to the game content if they can be misunderstood or not used at all. They are simply there by virtue of arbitrary technical decisions to make it easier or harder to work with the toys as data storage devices.
So, maybe #3 is a "maybe not."
| Requirement | Our best guess | |
|---|---|---|
| for data on the toy | for video game content | |
| 1. willfully | Maybe? | Maybe? |
| 2. circumvented | Maybe not? | Maybe not? |
| 3. a technological measure that effectively controls access (i.e., an access control) | Maybe? | Maybe not? |
| 4. to a copyrighted work | Maybe not? | Maybe? |
| 5. for commercial advantage or private financial gain. | Maybe not? | Maybe not? |
Talk recap

We talked about NFC toys, which are toys, which have NFC tags embedded in them.

We talked a little bit about them, about the toys-to-life genre of video games, and about NFC tags in general.

We talked about various off-the-shelf hardware and software you can use to explore these NFC toys, how that exploration can lead to determining read/write credentials, and how to write your own data to three different types of NFC toy.

Finally, we talked about the legal implications of doing so, and I have hopefully established that using NFC toys for your own data storage is probably not circumventing an effective access control, is probably not a copyright infringement, and that this work is legally enabling new interoperability of NFC toys with your own hardware.
While I discussed legal matters, I am not a lawyer, and this was not legal advice.

So, who believes that obtaining credentials for an NFC toy is legal, and wants to assert their right to do so? Raise your hands.
These are Amiibo cards, each card has an Amiibo NFC tag inside. Clipped to the card is a worksheet which explains how to compute the PWD for the Amiibo card longhand, I hope you'll enjoy working through it.

That's it for my talk, we don't have time to do Q&A, but I'll reply on nfc.toys to any questions submitted.
Please fill out your feedback forms, and pass them forward or hand them to me as you exit. Thanks so much.
References
Most references are linked inline. See the colophon for image attributions and credits.
The photo in slide 9 is by Matt Biddulph. I am a huge fan of his work going back to Reinventing Radio at BBC R&D, and I am right chuffed that this photo is a) his and b) just what I needed.
The NFC tag in slide 10 and 14 is from a Skylanders "Bash" figure, the same tag and toy seen disassembled in slides 34 and 181.
Slide 15's toys are Pokemon Rumble U figures, Nintendo's pre-Amiibo NFC toy from 2013.
Slide 16's toys are Star Wars Force Link, a series of action figures, vehicles, and playsets. You wear a wrist gauntlet which detects the NFC tags and plays sound effects appropriate to the character and/or its location in a play set.
Slide 17's toys are Beasts of Balance, a connected tabletop game. The stand is an NFC reader and digital scale which connects to a tablet over Bluetooth.
Slide 33's toys are Lego Dimensions, a toys-to-life video game where assembling and re-assembling the portal and the figures' accessories is part of the gameplay.
I am indebted to the hobbyists and researchers who went before me, and to everyone who publishes their notes, their documentation, and their software for others to learn from and build upon, but especially the Proxmark community, Adafruit's NFC and MIFARE explainer and the RFIDIOt Python library.
Questions and answers
For answers to questions submitted during the conference presentation, see the Q&A page.